Our team recently decided to reconfigure an old Windows Server 2012 group of servers/network to set it up for production use. We recently renamed the old domain for all the servers, reattached each server to the domain, and purchased and uploaded/configured a new wildcard certificate for the environment. One issue we have run into is references to the old domain name in various places. We have had to detach and reattach servers multiple times to get the desired result of an updated domain name (this was an issue in most cases). We appear to have been successful in this endeavor.
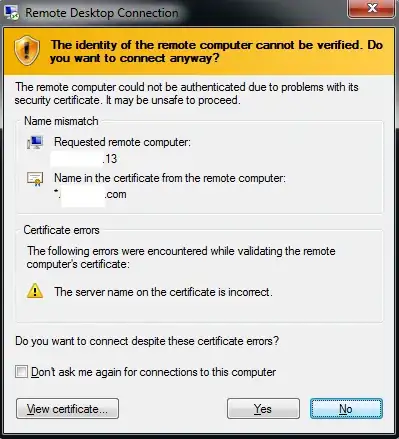
The current issue which I cannot resolve is an issue related to a name mismatch and certificate warning. In my case, I am connecting via VPN + private IP address + RDP to the server, but when I connect, the "requested remote computer" name is the private IP address of the server (ex. 10.20.30.20). It should instead be the FQDN of the server (ex. computername.blahblah.com). Since it simply sees an IP address for the server, the "name in the certificate from the remote computer" does not match up (the SANs within the certificate use computername.blahblah.com references).
Note that this mismatch is only occurring on one server in the group. All other servers behave as expected with a proper computer name which does match a SAN listed in the certificate.
How can I update the "requested remote computer" name of the server so that I do not get any more name mismatches with my certificate? See error screenshot below: