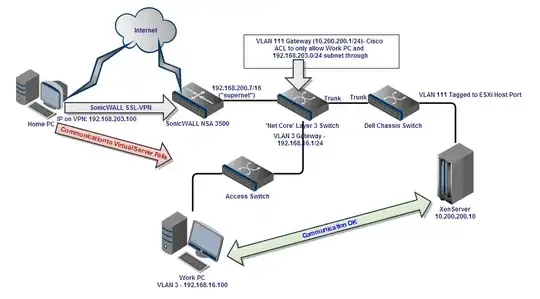
In the image above, we use the SonicWALL NSA 3500 at our gateway and handle VPN with its SSL-VPN. Our Layer 3 Cisco switch is our core network switch and handles about a dozen VLANs. Most VLANs are 192.168.x.x/24 variants, so the SonicWALL actually sees the rest of the network underneath it as 192.168.0.0/16 (we are "supernetting"). The Cisco does the actual routing (inter-VLAN routing).
But now I've created a VLAN on the Cisco of 10.200.200.x/24 where I have set up a XenServer. Both with and without the ACL (see image) applied, I can communicate just fine from my work PC but cannot ping the device from my Home PC through the VPN.
I have allowed 10.200.200.0/24 as a Client Route in the SSL-VPN settings, and attempted different routing table configs to get it to work, but have so far been unsuccessful.
How do I get communication between the SSL-VPN clients (192.168.203.x/24) and Cisco's VLAN 111 (10.200.200.x/24)?
Errors in picture: Called the server an ESXi host instead of XenServer host, and from Home PC it fails to XenServer, not to "Virtual Server."