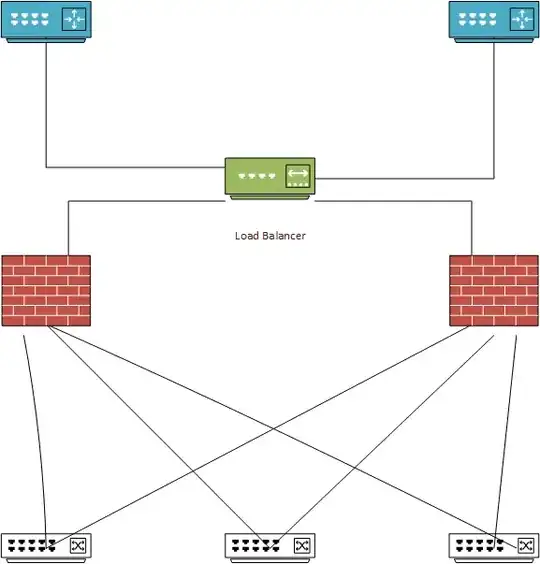
We're adding two SonicWALL NSA 2600 firewalls to our current setup. We currently get two WAN connections from two separate Cisco routers running on the same external subnet with what I believe is HSRP. Right now we run these two connections into two Cisco switches, and all of our computers then plug into both switches with NIC teaming.
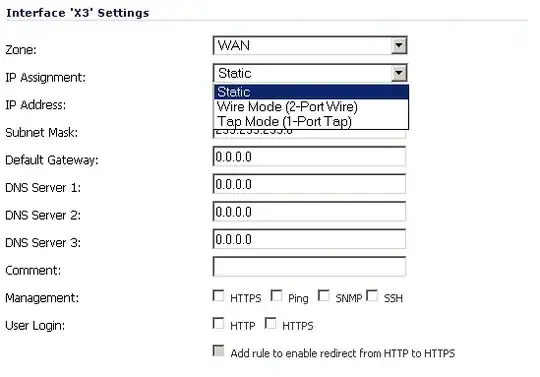
In the new setup, we'd like to create a 3-port VLAN on each switch, one port for the WAN connection from the Internet and two ports for each NSA 2600. I've got the WAN port setup from one switch to each SonicWALL in HA mode. If I add the second switch connections to X2, I can't figure out how get the bridged in the Network section. If I choose the WAN zone, I just get Static, Wire Mode, and Tap Mode. Static doesn't make much sense, since I'd need to pick a new IP address. Wire Mode will only let me choose unused interfaces (X4 and X5), and Tap Mode looks totally useless.
Does anyone have any tips on how to make this work or where to learn more about getting something like this working?
In case a diagram might help someone understand what I'm trying to do:
Here is what it looked like pre-firewall:
Here are pictures of what I'm seeing on my LAN side:
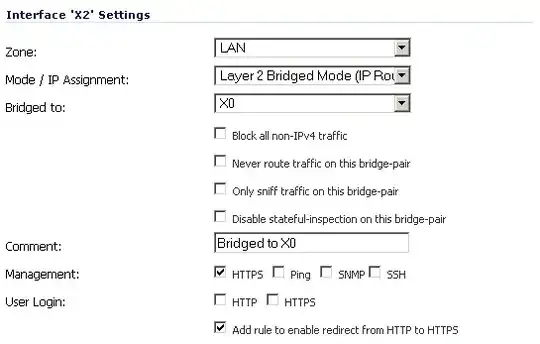
Nothing like that seems to exist on the WAN side: