I was wondering how to properly setup DNS forwarders on Windows Server 2008 R2. I have three Domain Controllers. Each of the DC's have have following:
- AD Role
- DNS Role
- DHCP Role
- Static IP Address
- Windows Server 2008 R2 SP1
- 64 Bit
I noticed under DNS Forwarders, that each DC only has one other DC listed and not both DC's. Here is a picture:
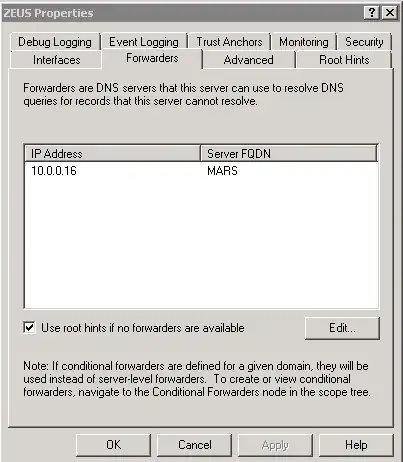
Is it correct to only have one DC listed, or should I list the other DC as well?