Does anyone know how to define a range of IPs to blacklist in the cPHulk Brute Force attack settings?
I am getting bombarded from IPS 103.26.193.* and 103.26.194.*
I Googled it and cannot find specific instructions or settings on IP Ranges
Step 1 - Entering a range with asterisk (*):
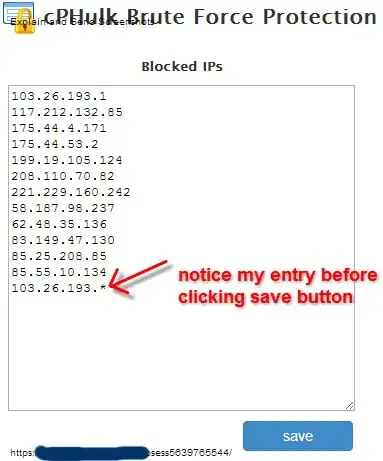
Step 2 - Updated the Blacklist (unsuccessfully):
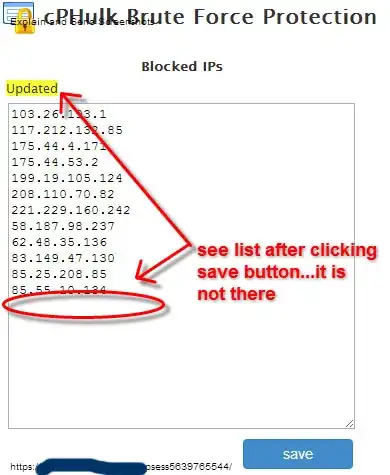
Follow @rholmes answer below and use these settings to block Foreign Hackers:
1.0.0.0/8
10.0.0.0/8
103.0.0.0/8
105.0.0.0/8
108.0.0.0/8
109.0.0.0/8
11.0.0.0/8
111.0.0.0/8
112.0.0.0/8
113.0.0.0/8
114.0.0.0/8
115.0.0.0/8
116.0.0.0/8
117.0.0.0/8
118.0.0.0/8
119.0.0.0/8
12.0.0.0/8
120.0.0.0/8
121.0.0.0/8
122.0.0.0/8
123.0.0.0/8
124.0.0.0/8
125.0.0.0/8
13.0.0.0/8
132.0.0.0/8
14.0.0.0/8
141.0.0.0/8
147.0.0.0/8
15.0.0.0/8
16.0.0.0/8
17.0.0.0/8
173.0.0.0/8
175.0.0.0/8
176.0.0.0/8
177.0.0.0/8
178.0.0.0/8
18.0.0.0/8
180.0.0.0/8
181.0.0.0/8
182.0.0.0/8
183.0.0.0/8
186.0.0.0/8
187.0.0.0/8
188.0.0.0/8
189.0.0.0/8
19.0.0.0/8
190.0.0.0/8
193.0.0.0/8
194.0.0.0/8
195.0.0.0/8
196.0.0.0/8
197.0.0.0/8
2.0.0.0/8
20.0.0.0/8
200.0.0.0/8
201.0.0.0/8
202.0.0.0/8
203.0.0.0/8
206.0.0.0/8
209.0.0.0/8
21.0.0.0/8
210.0.0.0/8
211.0.0.0/8
212.0.0.0/8
213.0.0.0/8
217.0.0.0/8
218.0.0.0/8
219.0.0.0/8
22.0.0.0/8
220.0.0.0/8
221.0.0.0/8
222.0.0.0/8
223.0.0.0/8
23.0.0.0/8
24.0.0.0/8
25.0.0.0/8
26.0.0.0/8
27.0.0.0/8
28.0.0.0/8
29.0.0.0/8
3.0.0.0/8
30.0.0.0/8
31.0.0.0/8
32.0.0.0/8
33.0.0.0/8
34.0.0.0/8
35.0.0.0/8
36.0.0.0/8
37.0.0.0/8
38.0.0.0/8
39.0.0.0/8
4.0.0.0/8
40.0.0.0/8
41.0.0.0/8
42.0.0.0/8
43.0.0.0/8
44.0.0.0/8
45.0.0.0/8
46.0.0.0/8
47.0.0.0/8
48.0.0.0/8
49.0.0.0/8
5.0.0.0/8
50.0.0.0/8
51.0.0.0/8
52.0.0.0/8
53.0.0.0/8
54.0.0.0/8
55.0.0.0/8
56.0.0.0/8
57.0.0.0/8
58.0.0.0/8
59.0.0.0/8
6.0.0.0/8
60.0.0.0/8
61.0.0.0/8
62.0.0.0/8
63.0.0.0/8
64.0.0.0/8
65.0.0.0/8
66.0.0.0/8
67.0.0.0/8
68.0.0.0/8
69.0.0.0/8
7.0.0.0/8
70.0.0.0/8
71.0.0.0/8
72.0.0.0/8
73.0.0.0/8
74.0.0.0/8
75.0.0.0/8
76.0.0.0/8
77.0.0.0/8
78.0.0.0/8
79.0.0.0/8
8.0.0.0/8
80.0.0.0/8
81.0.0.0/8
82.0.0.0/8
83.0.0.0/8
84.0.0.0/8
85.0.0.0/8
86.0.0.0/8
87.0.0.0/8
88.0.0.0/8
89.0.0.0/8
9.0.0.0/8
90.0.0.0/8
91.0.0.0/8
92.0.0.0/8
93.0.0.0/8
94.0.0.0/8
95.0.0.0/8
96.0.0.0/8
97.0.0.0/8
98.0.0.0/8
99.0.0.0/8
To complete the loop on buttoning your server down, refer to my other question here --> Do cPHulk Brute Force Protection Settings Effect Hosts?