I’m connecting over the web to a remote Windows Server 2012 R2 via Remote Desktop Connection for administration needs. It is a single web and database server without an AD etc.
I’m not talking about Remote Desktop Services / Terminal Server, just the simple Remote Desktop feature activated through Control Panel > System > Remote Settings. The server will automatically create a self-signed certificate to encrypt the connection and the Remote Desktop Connection client will show a certificate error due to the untrusted CA.
I have a CA signed certificate issued to the FQDN of this server and valid for server authentication (I’m using it for MSSQL Server remote access).
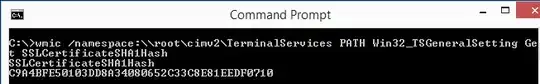
I’d like to use that one for RDP connections too. All tutorials (like this question) I’ve found so far describe the process for the Remote Desktop Services or Terminal Service. I have found this question stating a wmic command to set a certificate, but I don't want to try setting some values when I don't know what exactly I'm doing.
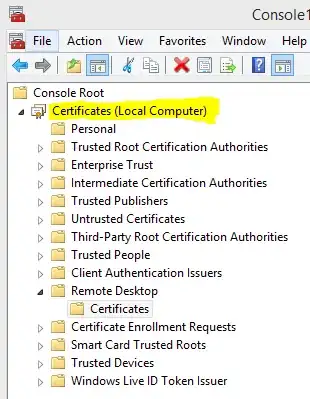
What I have done is adding it to the Remote Desktop Certificates of Local Computer where the auto generated self-signed is located too.
Is that possible? If yes, what do I have to do?
Thanks!