Is there a way to see /log which cipher suites are (actively) being used to establish SSL connections on Windows Server 2008 R2?
Ideally on a per request basis, like an extra column in the IIS logs.
Asked
Active
Viewed 8,117 times
8
Frederik
- 183
- 1
- 6
1 Answers
8
IIS logs won't help you here, since the SSL connection is negotiated before any HTTP/application layer traffic starts flowing.
But what you can do is:
C:\Windows\system32>netsh trace start capture=yes
Trace configuration:
-------------------------------------------------------------------
Status: Running
Trace File: C:\Users\Ryan\AppData\Local\Temp\NetTraces\NetTrace.etl
Append: Off
Circular: On
Max Size: 250 MB
Report: Off
C:\Windows\system32>netsh trace stop
Correlating traces ... done
Generating data collection ... done
The trace file and additional troubleshooting information have been compiled as "C:\Users\Ryan\AppData\Local\Temp\NetTraces\NetTrace.cab".
File location = C:\Users\Ryan\AppData\Local\Temp\NetTraces\NetTrace.etl
Tracing session was successfully stopped.
You can open that ETL file with Windows Performance Analyzer, and also with NetMon. (The latter will likely be more useful to you.)
Here's a screenshot of that trace file I just generated:
(Open in new tab to see fullsize)
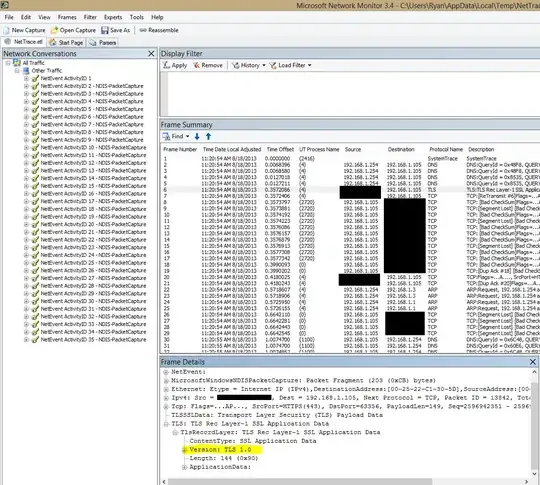
Edit: To find the exact cipher mode being used, locate the "HandShake: Server Hello" packets:
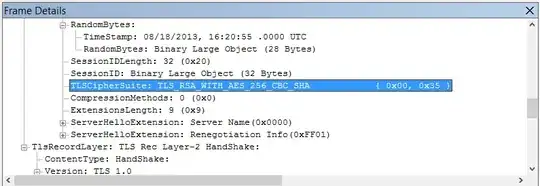
Here is a Microsoft support article telling you how to interpret the bytes of the packet manually, but Netmon will do it for you.
You could come up with a packet trace filter that only contained packets of this nature. If there's a better way to get this data I'd like to know about it.
Ryan Ries
- 55,011
- 9
- 138
- 197
-
Close. I origally accepted the answer, but I can't work out from this what actual cipher suite is being used. "TLS 1.0" is too vague. I can see in the handshake packet a bunch of suites being offered ("TLSCipherSuites: TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA { 0x00, 0x88 } etc", but I can't tell which one is being picked. – Frederik Aug 18 '13 at 18:18
-
For extra credit - I'd prefer something that grabbed less data than ETL - all I need is a historical log of ciphersuites used. – Frederik Aug 18 '13 at 18:22
-
1Edited my post. Yes the precise cipher mode is in there too. – Ryan Ries Aug 18 '13 at 21:11
-
What about constant monitoring to collect statistics about what protocol/suites are being used on server? Is trace appropriate to be running on webserver 24/7 performance wise? Ofcourse netsh can be limited to capture subset of traffic (like port, not sure if only TLS handshake can be filtered out), but what would be community opinion? – Janis Veinbergs Jul 02 '18 at 09:06