I'm having an hard time figuring out why can't I capture the packets flowing between two devices, in both directions, using a self made Ethernet tap, with copper cable, which looks just like this one:

Both end devices (say, A and B) are connected to a switch. But since the sniffer (a regular laptop) only has one Ethernet port I can't perform the sniffing, like it is presented in most cases (e.g. Wireshark Example using Network Tap), where the traffic from TX and RX is received on a Sniffer with 2 interfaces.
So, in order to "solve" this issue, I just plugged the 2 (tap) connector ports to the ones on the switch and, finaly, 1 port from the switch to the sniffer. I thought the packets would just be broadcasted but every time I plug the connectors to the switch the connection between A and B is interrupted (can't ping from A to B and vice versa). I made an illustration of the scenario:
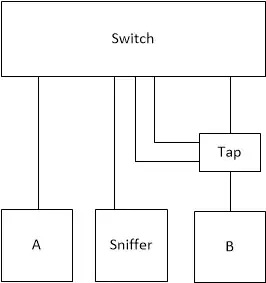
What kind of problem is the switch experiencing when I perform this connection? is it really necessary a commercial tap (those devices with 3 ports: A, B and sniffing port)?
Any ideas?
PS: I don't want to use port mirror or a hub. I want a passive tap.