This is a bit complex so bear with me. I do have a pretty good working knowledge of IP but I'm looking for help on the best way to implement this.
My ISP has given me a block of static IPs as well as a single IP. For privacy's sake, here's the network layout I'll be using in my examples:
- 192.168.1.0/24 - LAN
- 172.16.0.1/30 - Single static IP, default gw 172.16.0.2
- 172.16.1.1-5/28 - Range of static IPs, default gw 172.16.1.6
In these examples, 172.16.0.1 and 172.16.1.1-5 in reality are world-routable Internet IPs. I'm using private IP blocks for privacy's sake. So pretend that 172.16.0.1 is whatever public IP you want to imagine, and same for the 172.16.1.1 block.
My service is provided via a single cable modem interface with a single Ethernet port. In other words, all of the switching, routing, etc. is expected to be done on the customer side.
I currently have a Linux server with two Ethernet interfaces. It is assigned 172.16.0.1 static and uses NAT to provide Internet to the LAN interface, which works perfectly. I've used this setup for years to provide me with a NAT router that I have a lot deeper control over than an off-the-shelf router.
Now, I want to begin utilizing those other static IPs I have. The catches are these:
I still want to be able to, at least to some degree, control the access to those boxes. So, at the main Linux box, I'd like to be able to say that "172.16.1.1 cannot receive any incoming connections except via port 80" or "172.16.1.2 cannot connect outbound to anything except port 22". Just some examples. In other words, I still want firewall control over these boxes. Similar to how I can presently use
iptablesto block say 192.168.1.5 from going anywhere except where I want it, and in this instance, also counting the inbound connections as well. Ideally this would mean that I can get all packets destined for one of the five public statics routed via iptables and have the same level of control I do over LAN packets.Computers on the LAN (192.168.1.0/24) may need to access these public-facing machines as well. In addition, computers on the public IPS may need to access the LAN computers. So, 172.16.1.2 may need to access 192.168.1.5 and vice versa.
The computers that have static world-routable IPs should if at all possible be self-aware of their public-facing IP. One suggestion I saw for this suggested plopping the public computers on the LAN and giving them LAN addresses, then using multihoming on the Linux box and forwarding all ports from the desired static to the desired LAN IP. This certainly does work but it creates some messy situations - the Linux box now needs to be aware of every single static IP and thus this wouldn't scale well. So for instance "eth1" (the WAN interface) would need to not only have the IP that it already uses, but also all five other IPs. This might be fine for five, but what about scalability when in the future there's 2000 IPs....
One idea I thought of was adding a third interface to the Linux router and setting up a small network that contains only the public-facing machines. The only question then is routing between those machines and the Internet. On top of that, the only simple way I could think of to accomplish it this way was to give the Linux box a second IP address on eth2, which would use up one of those five precious statics.
I do not want to have to use any commercial solutions to accomplish this. I would feel Linux should be able to handle this sort of situation.
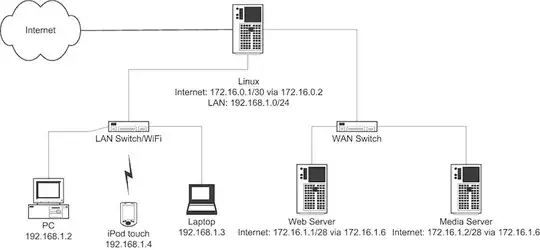 This is the layout I'm hoping will work but I just need to figure out how to do the routing itself on Linux.
This is the layout I'm hoping will work but I just need to figure out how to do the routing itself on Linux.