I'm having something weird happen on a Windows Server 2008 R2 server.
Every day at exactly 9:00 PM, an Audit Failure is registered in Event Viewer, saying that an account failed to log on for reason "Unknown user name or bad password.". The weird part is that the Account Name is a 161-character string, beginning with @@, the rest being a seemingly random string of characters. This name is the same every day. It seems to be coming locally from the server. The Logon Type is 4, the Caller Process is svchost, and under Detailed Authentication Information the Logon Process is Advapi, and the Authentication Package is Negotiate. Any ideas where this might be coming from? Any other relevant information I haven't provided?
- 243
- 2
- 7
-
Have you tried base64 decoding the seemingly random string after `@@`? – Mathias R. Jessen May 12 '13 at 11:48
-
@mathias Ah, no I have not. Any idea what I can expect to find there? I'll next be there on Sunday, so I'll check. – Micha May 13 '13 at 14:29
-
Hopefully a more sensible reference to a Security Principal of some sorts :-) - As @kce mentioned below, Scheduled Tasks seems likely because of the Logon Type (4). – Mathias R. Jessen May 13 '13 at 16:05
-
Okay, so it doesn't look like base64. A base64 decoder returned gibberish... Still not sure if the data is something sensitive or anything, but if it helps, this is the result of `ruby -e 'puts "string".split("").uniq.sort.join("")'`: 01456ABCDEFGHILMNOQUYZbceghkorstwy. Anything else I should try? Or do you think it's safe to post the string here? – Micha May 19 '13 at 06:53
-
1Have you checked your scheduled tasks yet? Logon type 4 is a batch logon, and most likely coming from a scheduled task (the fact it happens at the same time would also indicate that it's some sort of job). Can you post the complete event here, such as event id and any other relevant information? – Lucky Luke May 22 '13 at 18:52
-
@LuckyLuke The event data is here: http://pastebin.com/92GezLx6. Also, I went back and filtered by time in Event Viewer... I found this: Task Scheduler failed to log on "TaskScheduler:Task:{948A9ABA-1A81-4AEC-801D-3A05560AC928}" . Failure occurred in "LogonUser" . User Action: Ensure the credentials for the task are correctly specified. Additional Data: Error Value: 1326. I went into Task Scheduler, went into the task settings, and re-specified the username. When I clicked OK, I got a credential popup, and after entering the password, I got this: http://i.imgur.com/3HzfxVk.png – Micha May 23 '13 at 07:00
-
@MathiasR.Jessen Looks like I found the source of the problem. Now it's just a matter of figuring out how to fix it... – Micha May 23 '13 at 07:04
2 Answers
As it turns out, that was the Backup scheduled task failing to start. Apparently, at some point the Group Policy setting "Network access: Do not allow storage of credentials or .NET Passports for network authentication" got enabled. This was disallowing storing the credentials for use with the scheduled task, as seen in the error message: 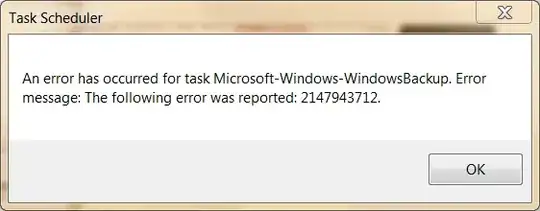
A quick Google search later, and the cause was revealed. I was able to specify credentials in Task Scheduler, and tomorrow morning I'll see whether or not the problem is solved. Still don't know where "@@CyBAAAAUBQYAMHArBwUAMGAoBQZAQGA1BAbAUGAyBgOAQFAhBwcAsGA6AweAkDA0AAOAEEA5AQQAIEABBQLAEDABBAOAEDAtAANAEEAFBwQA0CA4AAMAEDAEBQLAMDABBAMAUDA1AgNAADABBwQAkDAyAAOA0HA" came from, but hopefully that's no longer important. Thanks for all your help!
- 243
- 2
- 7
My first inclination is that this was caused by a Scheduled Task that was being run under an user's Active Directory account that was either disabled or deleted, however it appears it may be of more sinister origin.
Advapi appears to be part of BKDR_NETDEVIL.12 malware package so it seems likely that your server is compromised.
-
2`Advapi` is also an assembly pertaining to the Windows base API - It's not in itself all that sinister... – Mathias R. Jessen May 12 '13 at 11:45