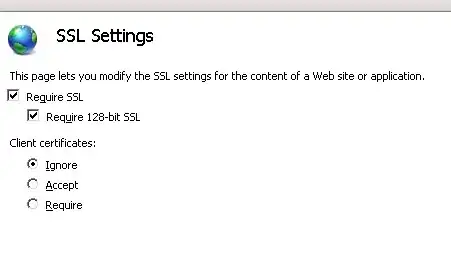
Below, in quotes, is a medium severity issue discovered after scanning an IIS web server, with a tool called Nessus.
"Consult the application's documentation to disable SSL 2.0 and use SSL 3.0, TLS 1.0, or higher instead"
I found this article, but I cannot find the "Server" folder. "Client" is the only folder listed on the machine I had scanned, under this registry path, HKey_Local_Machine \System\ CurrentControlSet\ Control\ SecurityProviders\ SCHANNEL\ Protocols\ PCT 1.0\. The OS is Windows Server 2008, x64. What steps do I need to take to fix this vulnerability?
http://support.microsoft.com/?id=187498
Does this have to be set a certain way?