This is an interesting question. I've never thought about data security at the hypervisor level... usually security policies and hardening revolve around OS-specific tasks (limiting daemons, ports, disabling core files, filesystem mount options, etc.)
But after some quick research (and running strings against active VMWare .vswp files) shows that it's definitely possible to extract data from .vswp files residing on a VMWare datastore. This link helps explain the lifecycle of such files.
In your case, I think your approach is going to be determined security policy and requirements. In my experience in finance and dealing with audits, I think that an accepted approach would be to limit/secure access to the host server. Recall that by default, your ESXi host does not have SSH or console access enabled. Enabling those features throws an event/alert in vCenter that needs to be manually overridden, so the assumption is that auditing access is the best way to control access to this information.
If there are concerns about who may have access to the server, there may not be a technical solution to an administrative problem. I'll check some other sources to see if there's a way to limit use of .vswp files, though.
--edit--
You can reserve all of the guest RAM. You don't specify which version of VMWare you're using, but in my 5.1 installation, there's an option to Reserve all guest memory. Enabling this option creates a zero-length .vswp file, rather than one equal to the size of RAM allocated to the virtual machine. Pay no attention to the vmx-.vswp file. That's new to ESXi 5.x, and it's not related to the guest's operating system memory pressure (it's for VMX process heap, guest peripherals and management agents). In addition, the vmx-.vswp files can be disabled by setting sched.swap.vmxSwapEnabled to FALSE.
I think this will give you what you're asking for.
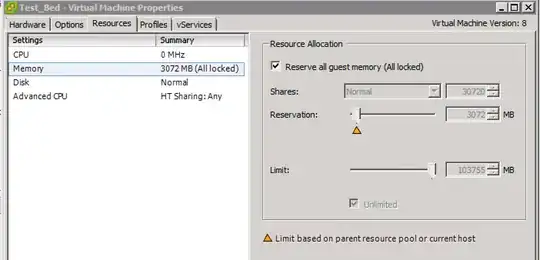
No memory reservation (default):
root@deore:/volumes/vol2/staging/Test_Bed# ls -al | grep vswp
-rw------- 1 nfs nobody 3221225472 Dec 23 13:31 Test_Bed-ad493981.vswp
-rw------- 1 nfs nobody 115343360 Dec 23 13:31 vmx-Test_Bed-2907257217-1.vswp
With memory reservation locked-in:
root@deore:/volumes/vol2/staging/Test_Bed# ls -al | grep vswp
-rw------- 1 nfs nobody 0 Dec 23 13:38 Test_Bed-ad493981.vswp
-rw------- 1 nfs nobody 115343360 Dec 23 13:38 vmx-Test_Bed-2907257217-1.vswp
Edit 20210711: Wayback Machine or Archive Today archived versions of the above links (of which some already were gone):
