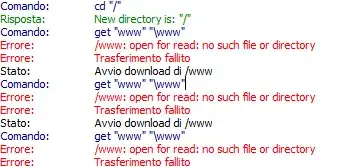
It's likely the SFTP is being chrooted, so that the directory /var/www is not available to the user in the chroot jail.
Look in /etc/ssh/sshd_config and examine the sftp directives. Do you see something like:
Match group sftp
ChrootDirectory /home/%u
AllowTcpForwarding no
ForceCommand internal-sftp
The sshd_config man page is here.
Basically, once the user is in /home/username in SFTP, that directory becomes / and references outside of /home/username are not available. In fact, a symlink like ln -s /var/www /home/username/www will look like you're trying to reach /home/username/var/www (i.e., /home/username is now / so any link that references /var/www must also be a subdirectory of /home/username in the context of the chroot).
As a solution, you can turn off the chroot (but this will have other security implications, mainly with SFTP users having full rein over your filesystem). You can do a loop mount of /var/www into /home/username/www (something like mount --bind /var/www /home/username/www (check your documentation for mount) which should work as you'd expect under chroot). You can also muck with the sshd_config file to exclude that one particular user from chroot (though, again, with security implications).
I would try the bind mount first.