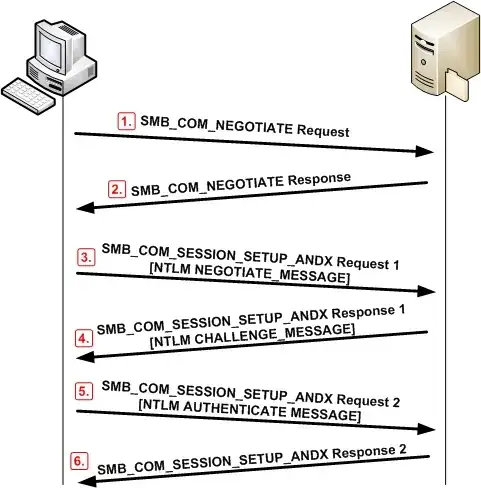
Environment:
- Windows 2000 sp4 EDIT: Domain Controller with no trust setup with the Win2008 Server
- Windows XP machines
- Windows 2008 Server
- Netapp NAS
Problem:
We have a shared folder that resides on a NAS using a Windows 2008 AD for the authentication with the proper permissions setup. When the Windows 2000 machine tries to open the share residing on the Win2008 machine, it is prompted for a username and password. Upon entering the credentials it continuously re-asks for credentials.
Important Details:
The Windows 2000 machine can ping both the XP machines and the Windows 2008 Server
The Windows 2008 machine is mandated to only use NTLMv2
The Windows 2000 machine was originally set to NTLM but was recently switched to NTLMv2 if negotiated for the purpose of trying to connect to the share.
As I am sure it will come up, we are using Windows 2000 because of contractual obligations
Questions:
Why is password Authentication failing in this case?
After setting a GPO for the Win2000 machine for it to use NTLMv2, we used SECEDIT to update the GPOs without rebooting. Does anyone know if this is sufficient or will a reboot be required?
UPDATE
We checked both of the 2008 Domain Controllers to find an error code. We received:
Microsoft_Auth_Package_V1_0
0xc000006a
Event ID: 4776
I know this to be an authentication error via THIS article
"The value provided as the current password is not correct"
We know this password to be correct, but since these two domains (Win2000 & Win2008) do not have a trust setup what authentication account needs to be used? One that resides on the Win2000 hosted domain?
Update 2
I have done some research into NTLMv2 and the settings that are required as the whole if negotiated thing was getting to me. I stumbled upon the following information:from the following source:
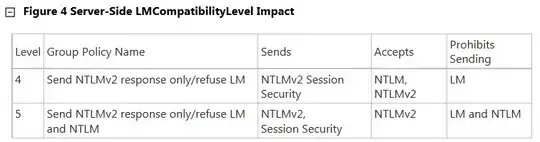
So my question then is still the if negotiated and what the true meaning of session security when dealing with NTLMv2? My thinking is session security are the keywords here.
Our 2008 server is set to level 5 Our 2000 server is set to level 1
The 2000 server cannot under any circumstances be changed from level 1 as unfortunately it would break authentication to many legacy devices. So to me it sounds like the issue is at level 3 where the session is passing NTLM.
I feel like I am almost there but I am having a difficult time processing through it.