I'm having an issue testing a hardened SSL configuration for pound.
One of the requirements is for the inclusion of AES[128|256]-SHA256 ciphers, along with strict ordering of preference. I've installed OpenSSL 1.0.1c-fips on CentOS 6 (via the IUS repos), and rebuilt pound against it (along with a patch for order honouring).
My pound cipher configuration contains six ciphers, and reads:
Ciphers "RC4-SHA:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA"
SSLHonorCipherOrder 1
On my local machine (Ubuntu 12.04, running OpenSSL 1.0.1), I have a script which tests every cipher locally supported against the website, and reports the results. The abbreviated output is:
~$ ciphertest.sh x.x.x.x:443 | grep YES
Testing AES256-SHA...YES
Testing DES-CBC3-SHA...YES
Testing AES128-SHA...YES
Testing RC4-SHA...YES
You can see the SHA256 ciphers are not working. However I can confirm my local OpenSSL does have AES256-SHA256 support:
~$ openssl ciphers -v | grep ^AES256-SHA256
AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256
I thought this was a configuration issue, until I ran a ssllabs.com test, which reports all 6 ciphers fine:
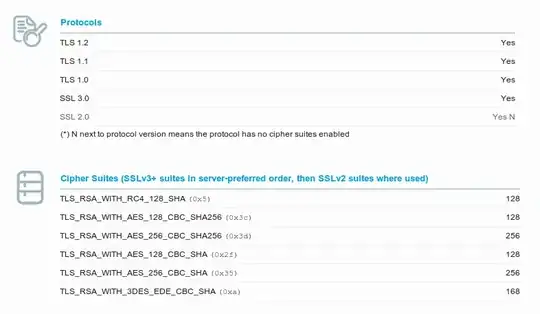
So can anyone explain why my openssl tests are failing to connect using SHA256 ciphers?