How can I check if my IIS site is using NTLM or Kerberos? And how can I change authentication from Kerberos to NTLM? I'm using IIS 7.5.
6 Answers
From:
Determine if HTTP authentication is NTLM or Kerberos
http://support.microsoft.com/kb/891032
[...] "Since we are looking over this trace to see if the client is sending authentication information, we can use the TCP segments to track the HTTP GET requests and the response from the server. Here is a snippet from the frame that sends authentication information from the client:
23 4294967263.4294641621 LOCAL 00045A420DBC HTTP GET Request (from client using port 3135) 192.168.0.2 192.168.0.4 IP
HTTP: GET Request (from client using port 3135)
HTTP: Request Method = GET
HTTP: Uniform Resource Identifier = /webapplication1/webform1.aspx
HTTP: Protocol Version = HTTP/1.1
HTTP: Accept = image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/vnd.
HTTP: Accept-Language = en-us
HTTP: Accept-Encoding = gzip, deflate
HTTP: User-Agent = Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR
HTTP: Host = alien
HTTP: Connection = Keep-Alive
HTTP: Authorization = Negotiate TlRMTVNTUAABAAAAB4IIogAAAAAAAAAAAAAAAAAAAAAFASgKAAAA
44 77 3D 3D 0D 0A 0D 0A AAADw==....
"What does this tell us? We can see that the Authorization header is set to "Negotiate" and we can see a long string of characters sent in that header. This response tells us that the client and the server are negotiating an NTLM connection. We know that NTLM authentication is being used here because the first character is a '"T." If it was a "Y," it would be Kerberos. The header is set to "Negotiate" instead of "NTLM." This does not mean it will use Kerberos or NTLM, but that it will "Negotiate" the authorization method and try Kerberos first if it is able. If it cannot use Kerberos, it will use NTLM."
// if it is Negotiate...
if (String.Compare(Request.ServerVariables["HTTP_AUTHORIZATION"].Substring(10, 1), "Y", true) == 0)
{
// we are using Kerberos
}
else
{
// we are using NTLM
}
- 103
- 3
- 34,339
- 3
- 52
- 81
-
1I'm getting the first characters as oXcw, any idea what that means? Maybe a newer version of kerberos? – Mark Adamson Sep 25 '17 at 19:57
-
2@MarkAdamson Me too, mine is oYG2... – Brain2000 Dec 12 '18 at 18:32
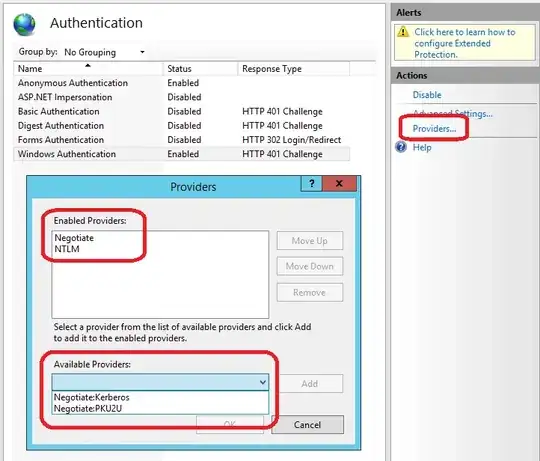
If you have access to your IIS server then the answer is much simpler than inspecting HTTP traffic: Simply view the site Authentication module config for Windows Authentication.
- In IIS Manager
- Select your site
- Click on the Authentication module
- Select Windows Authentication
- Select Providers...
- 2,504
- 3
- 12
- 15
Found out that microsoft has a really good page about Kerberos.
Here are a lot of pitfalls description when you use Kerberos and Negotiation (for example on localhost the Negotiation use NTLM as default).
If you used dotnet core the server code can looks like that (the code from @pafreire is for the old classic asp and also descripted on the ms page).
private string GetAuthMethodeInfo()
{
var authType = this.HttpContext.GetServerVariable("AUTH_TYPE")?.ToUpper() ?? string.Empty;
var authHeader = this.HttpContext.GetServerVariable("HTTP_AUTHORIZATION");
var lenAuthHeader = authHeader?.Length;
var protocol = authType.Length == 0 ? "Anonymous" : authType != "NEGOTIATE" ? authType : lenAuthHeader > 1000 ? "Kerberos" : "NTLM";
return $"Authentication-Method : {authType} Protocol: {protocol}";
}
- 11
- 1
use the code below in html/asp page:
<%
authType=UCase(Request.ServerVariables("AUTH_TYPE"))
authHeader=Request.ServerVariables("HTTP_AUTHORIZATION")
response.write " Authentication Method : " & authType & "<BR>"
LenAuthHeader = len(authHeader)
response.write " Protocol : "
if Len(authType ) =0 then response.write " Anonymous" else if authType<>"NEGOTIATE" then response.write authType else if LenAuthHeader>1000 then response.write "Kerberos" else response.write "NTLM"
%>
- 237,123
- 42
- 477
- 940
- 11
- 1
In your HTTP Request Header (you can see it from Firebug, Chrome Dev Tool or Fiddler) you will see something like this if you use NTLM
Authorization: NTLM=TlRMTVNTGD6XAAAAGAAYAG425qAAYABgAhgAAAAAAAABIAAAADgAOAEgAAAAYABgAVgAAAAAAAACeAAAABYKIogUBKAoAAAAPcwBpAG0AcABsAGkAcABOADMAUgBXAEsAVwBBAEwAVABFAFIAQQAzVtleqNj7HAAAAAAAAAAAAAAAAAAAAACW3g66aPaiileWScIYweBj6fs2iGY/ta3=
From IIS management panel, you can go Authentication and choose the authentication you prefer.
That answer isn't quite complete. There are two ways the connection can use NTLM. One is via the WWW-Authenticate method "NTLM"; the other is via Negotiate. Negotiate uses GSSAPI, which in turn can use various mechanisms; on Windows, this includes both Kerberos and NTLM.
Wireshark can decode all of this and show you quickly what's going on, assuming you're not using TLS. If you are, you can arrange that Wireshark be able to decrypt the TLS traffic; it just takes some extra effort.
- 794
- 4
- 7