There's a new tool and service that makes it very easy to break MS-CHAP v2, which is used to secure VPNs. A good summary of the attach against MS-CHAP can be found at Ars Technica. Here's the way I currently have my VPN service running on Windows 2003 R2 SP2 configured:
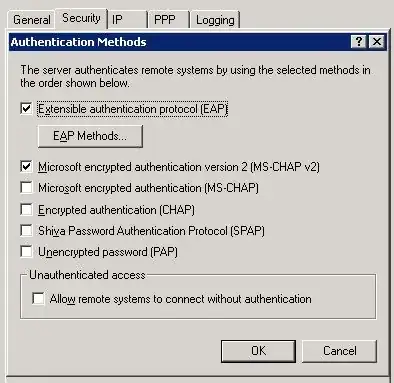
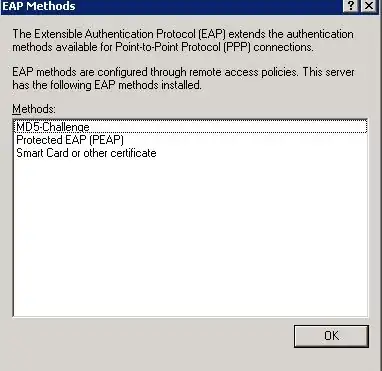
Should or can I just go with EAP? My client machines that use the VPN are Windows-XP (a small number of machines which I could turn off), Windows 7, and iPads. I don't have any RADIUS routers or wifi or anything else that relies on the Windows VPN service. The EAP methods that my machine has are: