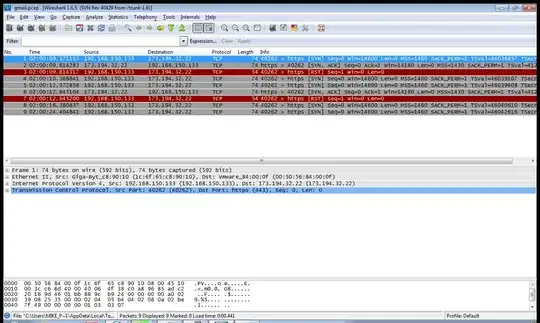
I am suspicious that my country's government is destroying the received ACK packet on TCP connections, somehow.
When I try to establish a TCP connection to an outside host on ports other than 80 the TCP handshake will not be successful. I captured the pcap file (gmail.pcap : http://www.slingfile.com/file/aWXGLLFPwb ) and I found out that my computer will receive the ACK after sending TCP SYN but instead of replying with a SYN ACK it will send an RST.
I checked the ACK packet from outside host, but it seems completely legit. The sequence number and all the flags that I am aware of, are correct. Could anyone tell me why my computer (a linux machine) will send the RST packet?