I am trying to setup a basic PPTP VPN connection using Forefront TMG 2010. Whenever I try to connect to the VPN connection from my Windows 7 machine, I get an error related to unauthorized access.
So went on to reconfigure allowed users for VPN.
Here is I found which might explain the problem:
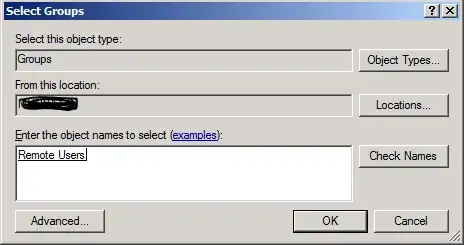
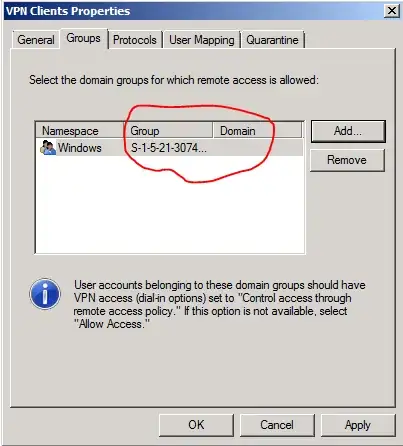
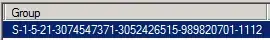
As you can see in the image above, the Group name is no longer Remote Users but rather a long string. And the Domain is missing entirely.
Could you please help me figure out the reason for it?
I would really appreciate any help you can provide me :)
Thanks a lot for looking into it.