I'm using OpenSWAN to set up a net-to-net VPN tunnel. I have succeeded in configuring a test scenario as follows:
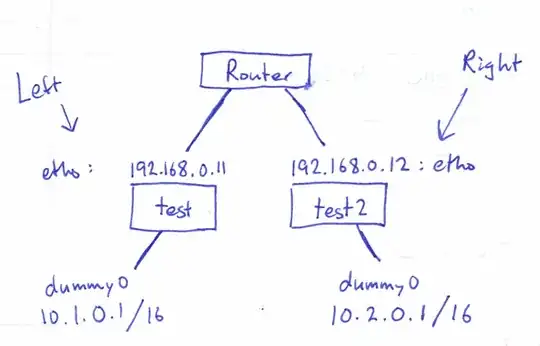
About test and test2:
- they are Ubuntu 12.04 virtual machines created using ubuntu-vm-builder
- they use bridged networking to the host's physical ethernet (the 192.168.0.0/24 subnet).
- I installed the standard
openswanpackage. - each has a dummy interface which is accessible from the other end of the VPN tunnel.
This is how I configured the tunnel:
/etc/ipsec.conf (identical on both left and right):
version 2.0
config setup
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
protostack=netkey
conn net-to-net
authby=secret
left=192.168.0.11
leftsubnet=10.1.0.0/16
leftsourceip=10.1.0.1
right=192.168.0.12
rightsubnet=10.2.0.0/16
rightsourceip=10.2.0.1
auto=start
/etc/ipsec.secrets (identical on both left and right):
192.168.0.11 192.168.0.12: PSK "mytestpassword"
/etc/rc.local (on left):
modprobe dummy
ifconfig dummy0 10.1.0.1 netmask 255.255.0.0
iptables -t nat -A POSTROUTING -o eth0 -s 10.1.0.0/16 ! -d 10.2.0.0/16 -j MASQUERADE
echo 1 > /proc/sys/net/ipv4/ip_forward
for each in /proc/sys/net/ipv4/conf/*
do
echo 0 > $each/accept_redirects
echo 0 > $each/send_redirects
done
/etc/init.d/ipsec restart
exit 0
/etc/rc.local (on right):
modprobe dummy
ifconfig dummy0 10.2.0.1 netmask 255.255.0.0
iptables -t nat -A POSTROUTING -o eth0 -s 10.2.0.0/16 ! -d 10.1.0.0/16 -j MASQUERADE
echo 1 > /proc/sys/net/ipv4/ip_forward
for each in /proc/sys/net/ipv4/conf/*
do
echo 0 > $each/accept_redirects
echo 0 > $each/send_redirects
done
/etc/init.d/ipsec restart
exit 0
Now, I would like to set up the following scenario:

Issues I need to understand:
- Can IPSec connect through a VPN gateway which is sharing a public ip via NAT (inbound NAT traversal)? Do NAT-T and IPSec passthrough relate to this or are they just for outbound NAT (i.e. dealing with clients which are behind NAT but where the gateway has a public IP)? Would it be sufficient to forward some ports from router1 to test, or would that be incompatible with IPSec?
- Can both ends of an IPSec tunnel have dynamic IP's as long as one has a domain name and dynamic dns?