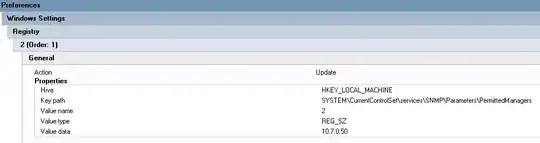
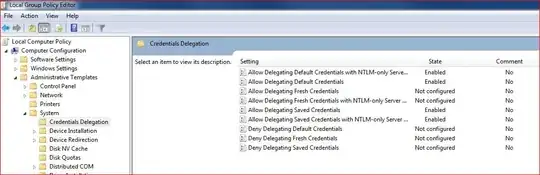
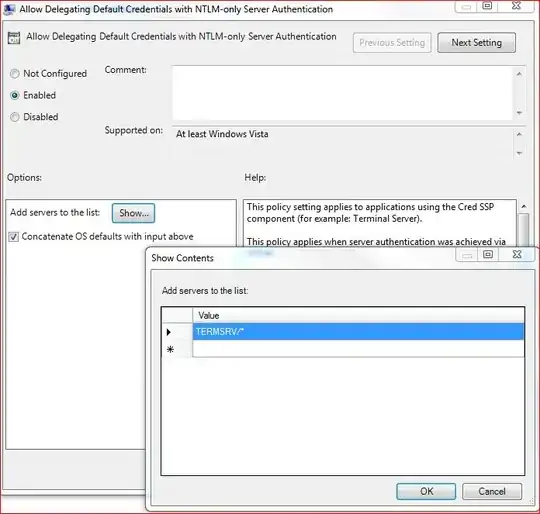
For those who are willing to add it directly to the registry, save the following content in a *.reg file:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation]
"AllowDefCredentialsWhenNTLMOnly"=dword:00000001
"ConcatenateDefaults_AllowDefNTLMOnly"=dword:00000001
"AllowDefaultCredentials"=dword:00000001
"ConcatenateDefaults_AllowDefault"=dword:00000001
"AllowSavedCredentialsWhenNTLMOnly"=dword:00000001
"ConcatenateDefaults_AllowSavedNTLMOnly"=dword:00000001
"AllowSavedCredentials"=dword:00000001
"ConcatenateDefaults_AllowSaved"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowDefaultCredentials]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowDefCredentialsWhenNTLMOnly]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation]
"AllowDefCredentialsWhenNTLMOnly"=dword:00000001
"ConcatenateDefaults_AllowDefNTLMOnly"=dword:00000001
"AllowDefaultCredentials"=dword:00000001
"ConcatenateDefaults_AllowDefault"=dword:00000001
"AllowSavedCredentialsWhenNTLMOnly"=dword:00000001
"ConcatenateDefaults_AllowSavedNTLMOnly"=dword:00000001
"AllowSavedCredentials"=dword:00000001
"ConcatenateDefaults_AllowSaved"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowDefaultCredentials]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowDefCredentialsWhenNTLMOnly]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials]
"1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly]
"1"="TERMSRV/*"
I got it by doing it manually and then searching the registry for TERMSRV.