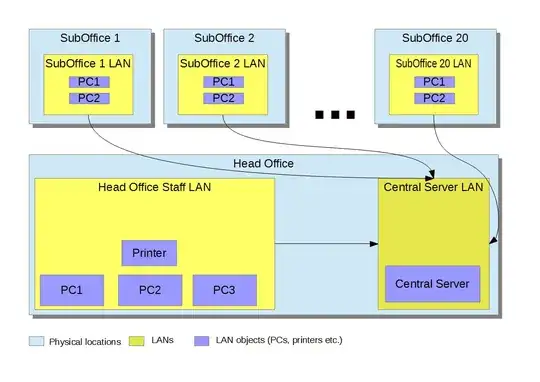
I have a head office and a number of suboffices. Both head office and suboffices need to access some corporate server, which is physically in the head office. But suboffices should not be able to access head office or each other. Suboffices are at the substantial distance of each other and from the head office (many kms).
How do I design the network for this task?
I suppose, each suboffice should have internet access. Central Server LAN switch should have static IP and OpenVPN software installed. For example, SubOffice1 network is 10.0.1.x, SubOffice2 10.0.2.x etc, Head office 10.254.x.x, Central Server LAN 192.168.0.x.
When suboffice PC or head office PC needs to access Central Server, a PC starts VPN connection for this to the central server.
I should then use routers for each network and setup firewall so that it permits connections from inside network only except for the Central Server LAN router.
Is this correct? May be there are some important details I should keep in mind building this network? What hardware would you recommend for this (routers, supporting needed firewalling modes etc)?
ADDED 07/05/2012:
Our ISP can provide nothing except for Internet access. I cannot expect them to support anything like MPLS. ISPs are different in each suboffice and head office.
The number of suboffices are like 20.
Connections from suboffices into the head office needs to be encrypted because it will be routed through internet.
I want suboffices to be isolated from head office and from each other completely so that no packet can travel there and back.
I plan to have only Linux PCs in the offices, but there can be also some Windows machines. No Active Directory or something. Just a PC under Windows/Linux.
Any good books out there on the subject?