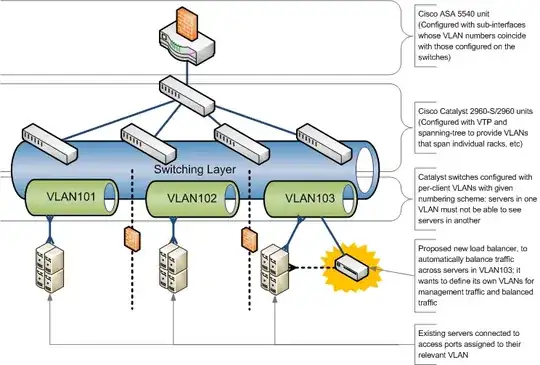
I have an existing firewall+switching layer which is separated into per-client VLANs, with its own numbering strategy, etc. This layer is interconnected by trunk ports such that VLANs numbered on one switch are honoured on any other.
One of my clients now wants to introduce a load-balancer into their VLAN. This device also designates VLANs (e.g. to separate management traffic from balanced traffic). We still require their traffic to be separate from all other clients (which is why we have the VLANs in the first place), so it is my intent to allocate them standard access switch-ports, assigned to their VLAN, as we would if it were just another server.
I don't quite have enough test equipment in my lab to do a full workup of this, so my question is really, will it work?
More specifically:
- Would a VLAN-defining device with its own VLAN strategy, plugged into an access port with my VLAN strategy cause cross-pollution of either strategy?
- Does the traffic coming from that VLAN-defining device just get encapsualated twice, firstly with its own VLAN tags, then with the switching layer's VLAN tags, and could that reasonably be expected to unwind correctly (e.g. for reply traffic)?
- Given that the servers will also be connected to access ports on the same client VLAN in the switching layer, will there be any difficulty with the load-balancer communicating with the servers?
- Even though I am looking for the balancer to reside on an access port in the switching layer, do I have to assign the balancer's VLAN numbers to specifically coincide with or diverge from the switching layer's VLANs?
- If, instead, I was looking to provide load-balancing services to multiple clients using the same balancer, is it just a case of configuring the VLAN numbers to coincide and configuring the interconnected switch and balancer ports as trunk ports?
(If it matters, the devices in question are all Cisco: ASA5540+Cat2960 at the firewall+switching layer, ACE4710 for the balancer)
Addenda