I am working on a Freeradius backed 802.1.x authentication infrastructure for our wireless clients. I am using a rather generic Freeradius configuration with EAP-PEAP. Our clients are predominantly Windows XP SP3 machines but a few Windows 7 32 and 64 bit laptops also exist. Our domain is at the Windows Server 2003 functional level. 802.1x authentication is working with manually configured test clients.
I want to create a GPO that autoconfigures our clients by 1) deploying the self-signed CA certificate to them as a Trusted Root Certificate, and 2) sets up our ESSID as a preferred network with the appropriate 802.1x configuration.
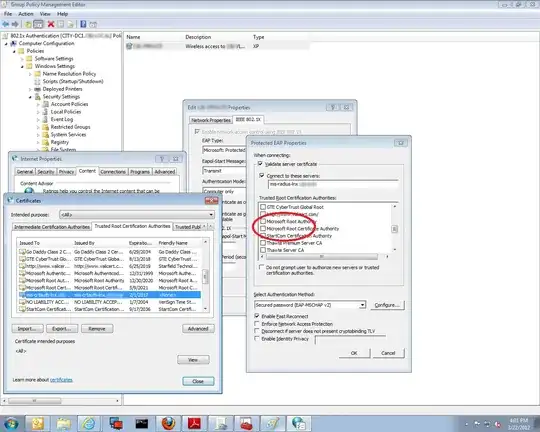
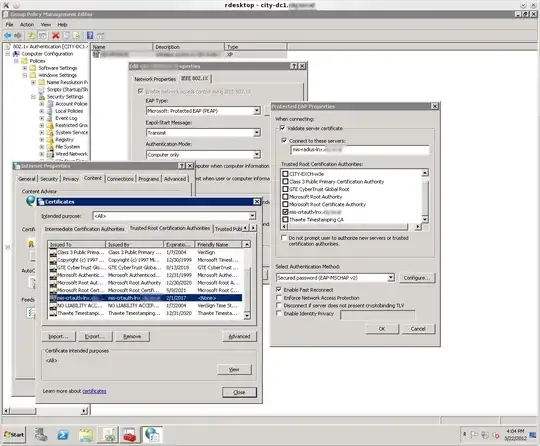
I am having no difficultly deploying the self-signed CA certificate to clients using a GPO. However, I cannot figure out how to configure the certificate as a Trusted Root Certificate in the GPO.
This is from the GPO settings found under Computer Configuration - Polices - Security Settings - Wireless Network (IEEE 802.11) Polices:
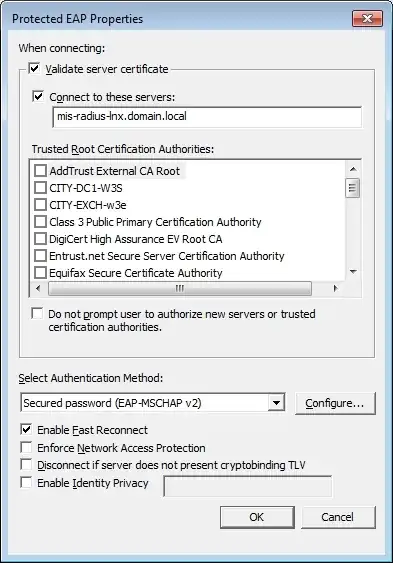
My self-signed CA certificate is not available in the selections under Trusted Root Certification Authorities. Trying to authenticate the client without my self-signed cert being trusted in the 802.1x PEAP settings fails due the "Validate server certificate" setting. And of course if I manually configure the client to trust my cert, the radius server's certificate can be properly validated and then 802.1x works.
My goal is to be able to assign a machine to OU where this GPO will be applied and all the resulting 802.1.x and CA settings will be made without me having to touch the client machine at all.
How can I build a GPO for 802.1x PEAP settings that will set clients to trust my self-signed CA certificate?
EDIT:
A Microsoft NPS or NAP server is not really an option for my organization at this point due to cost issues. The best way to describe our environment is a centralized location running our core services with two dozen remote sites connected via WAN links of varying speeds and reliability. We have a varying ability and success of exercising positive physical or policy control over these remote sites, hence they are my primary focus for both wireless and eventually wired 802.1x authentication. If we loose a WAN link (which happens not infrequently) I still need clients at remote sites to be able to get network access, thus necessitating a RADIUS server at most of these locations. A request for another dozen Window Servers will be denied.
Historically all of our Linux servers and network gear have been maintained as separate from our domain infrastructure. This means things like a split DNS scope with independent DNS services, independent authentication infrastructure and so-on. While I realize they're are some advantages to an domain integrated PKI infrastructure, I would need a good case as to why I should do it or or alternatively why I shouldn't use an independent PKI infrastructure.