I understand the basics of spanning tree, but that's about it. I'm hoping that someone can tell me if this will work as I want it to.
I've got two Cisco ACE load balancers setup for redundancy. Each ACE is connected to its own layer 2 switch. Currently each layer 2 switch is connected to its own 1 Gig fibre link to the CoLo. Each fibre link is setup for a different IP Subnet and our CoLo doesn't offer handling the BGP for us. We have to purchase our own routers to handle that, which is a project which is coming up.
(I've got the layer 2 switches in there because the CoLo provides fibre and the ACEs only have copper so all the switches are doing is changing the fibre to copper for me.)
So currently I can only use a single load ballancer because the ACEs don't support spanning tree. Now the layer 2 switches to support spanning tree, it is just disabled by default. Now if I were to enable spanning tree, and cross connect the layer 2 switches would everything work as expected, or would this cause the network to come crashing down?
I'm hoping to get some expert advise before I try this as it is a production network and I don't have a couple of extra Cisco ACE load ballancers to try it with in a lab.
UPDATE:
based on the comments I need to include a diagram. Here's what we currently have.
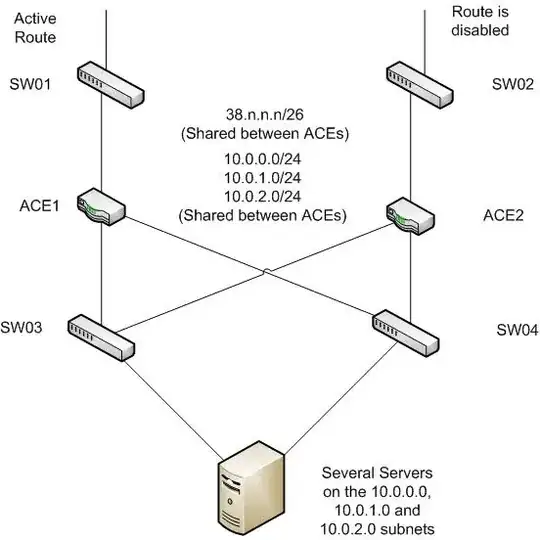
The problem is that the second ISP link isn't usable to us at the moment because of the lack of BGP. So I want to cross connect the two network switches together. I've been told that if I connect the two ACEs together that'll complete the circle and cause network problems. So if I can connect the switches at the top which support spanning tree that should take care of the problem. Eventually there will be two routers between the top switches and the load ballancers to handle the BGP over the two network links.
Am I making sense? Sorry this is such a mess, I'm much more at home in SQL Server then Networking.