I'm suspecting that one of my servers is attacked some time ago. My question is how can I identify a DOS or DDOS attack while under attack or after the attack has finished?
4 Answers
Denial of service attacks focus on consumption of a finite resource. Mostly that refers to network traffic, but it could be anything that you can run out of. For example, if your web servers take five seconds to generate a certain complex page, I can save myself a lot of traffic generation and just make a lot of requests for that slow page which rapidly consumes the server's back-end resources.
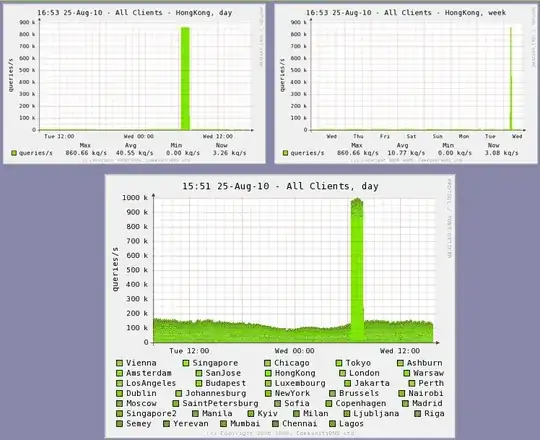
A denial of service attack is identified by seeing a big spike in resource use. If you look through a graph and see it spike hard, that's a candidate for a denial of service event.
Just because you see a lot of traffic or resource use doesn't mean it's an attack. The Slashdot effect explains that phenomenon. You'll only be able to figure that out by looking at your logs. If half the connections have referrers pointing to a legitimate article that was just posted on a major site, then it's real traffic. If not, perhaps you are under attack.
The difference between a DOS and DDOS attacks comes down to the challenge of "shutting off the valve." If it's not a distributed attack, I can just kill the offending host or network at a network edge and life will go on. When an attack is distributed, that's a much greater challenge. It's even further a challenge if your attacker makes an effort to make the unwanted traffic look very similar to your normal traffic.
Summary
- See spike
- Identify reason
- Identify responsible traffic
- 20,239
- 2
- 61
- 85
-
Personally, I consider a site suffering from slashdot effect to be under DDoS. Remove the malice motive and that's essentially what it is! The treatment is also essentially the same. – SimonJGreen Mar 05 '12 at 23:46
This depends on the services you are running. Wikipedia has a nice definition on it:
A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer or network resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person, or multiple people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely.
The term is generally used relating to computer networks, but is not limited to this field; for example, it is also used in reference to CPU resource management.
When you are running a web server you would see a huge spike in GET-requests, for DNS services this would bee lookups, ... The attack consists mostly off asking a lot of your server until the point it wouldn't be able to cope.
- 17,761
- 6
- 62
- 81
-
2You obviously like green - to the point it makes your graphs a bit pointless :-) – Coops Mar 05 '12 at 22:04
Determining the difference between a deliberate, malicious action and a non-malicious but nonetheless damaging action is difficult.
You see a large number of half-open connections in the SYN_RECV state. Are you being SYN flooded or has someone you work with changed a firewall rule or outbound routing rule?
You see a large spike in the number of HTTP requests from a single IP address. Is it a badly behaved bot or a script kiddy trying to DoS you from his mother's basement? Or maybe an email just went out to all the students at a University with a link to your website.
You see a large spike in the number of HTTP requests from many IP addresses. DDoS or Reddit?
You see a large number of DNS requests from one IP address. Is that server trying to DoS you or is someone else spoofing the source address to make you part of a reflected DNS attack?
There can be several hints as to whether your site is down due to a deliberate attack or organic traffic. Some of these can be determined from logs, some only while the attack is happening.:
As Jeff Ferland mentioned, a valid Referer header is a good hint that the traffic is legitimate however this is not absolute proof. A mildly popular page with hundreds of hidden images hotlinked from your site could be a method of initiating a DDoS. It doesn't even have to be images, any page will do. <img href="http://target-site.com" /> will still cause the client to load that page from your web server but display a broken image icon. If you find referrers, check out the page if you can and make sure it's really legitimate.
Email clients don't usually set a referrer but webmail clients do. Although you won't be able to see the email simply by loading the referrer, the fact that there is one suggests it is a legitimate request.
The User-Agent header can be a good clue. Most legitimate bots use unique user-agents with a link to an about page. Lots of not-so-legitimate bots (spam bots and email scrapers) use IE 6.0 as their user-agent. Most DoS tools contain a list of real but older user-agents from the most popular browsers that they rotate after each request. If you know the normal ratios of the different versions of each browser on your website, large spikes of Firefox 7.0.1 and IE 8.0 should stand out clearly. Especially since Firefox and Chrome auto-self-update now, seeing a version that's even a month old is rare.
DoS tools can request a single page or rotate through a list of pages but in either case, they don't normally request all the associated content such as stylesheets, javascripts and images. They also don't send cache control headers such as If-Modified-Since and If-None-Match since these largely defeat the purpose of making the request. If you see a lot of clients exhibiting this behaviour it's likely to be malicious. (As long as your cache controls are set up correctly.)
DoS tools often don't send the same headers as normal web browsers. Run a tcpdump on your server to capture some traffic and analyse it. Some differences I have seen in bots (not necessarily DoS tools):
- The
Host:header last instead of first. Normal browsers seem to list it right after the GET. - POST data not correctly URL-encoded. Some real browsers such as IE6 don't get this right either.
- Specific and unique
Accept-*:headers. Chinese and Russian languages jumped out at me but this is anecdotal, not statistical. - No Cookies.
Some headers can be clearly malicious, such as a Range: header that lists thousands of overlapping ranges.
If you have mod_forensic switched on you may be able to analyse these headers after the attack however mod_forensic can produce a lot of data in your logs and this could cause a DoS on its own.
As for the reflected DNS attack, it's pretty much impossible to tell by simply analysing the traffic. You will have to go out-of-band to figure this one out. Find out who owns the IP address and email them or phone them and ask if they really are making all those DNS requests.
Which brings me to the out-of-band methods of figuring out malicious intent. Often, there is a reason behind a DoS attack. Google can help you find that reason. Search for your domain name (but remove results from that domain with -site:yourdomain.com) and/or IP address and limit the results to the most recent ones. You may find evidence of the attacker boasting about taking you down or a tweet from @anonops signalling that you are the current target. You might also find the Slashdot story that mentions you. Either way, searching for your website may work. Don't forget the other search engines too, they all have their own crawlers and since you're looking for results from within the last few hours none of them will have complete coverage.
Some DoS attacks are based around extortion. Particularly against sites with a lot of money and specific, scheduled events such as gambling sites. The normal method is to generate a short DoS a week or two before the Super Bowl or the Grand National and follow it up with a threat that they'll do it again at the critical period if they aren't paid off. If you receive an extortion request, it's probable that the DoS was deliberate and malicious.
- 25,847
- 7
- 57
- 90
Simple direct answer to a simple direct question:
Set up monitoring on your router to graph the packets per second (pps). If you can't graph pps then graph bandwidth usage. I suggest using a package like Cacti to do this, very simple with Cisco gear and also local network interfaces.
Once you have that running you can watch out for spikes in pps.
If it's a simple DoS you can block the source of the traffic quite easily by firewall rules.
If it's a DDoS then unless you have some pretty hefty gear yourself you will need to have your IP transit provider pass the effected Route through a DDoS filter/protection service. Most transit providers offer this service.
- 3,195
- 5
- 30
- 55