The server works fine via the Amazon assigned DNS entry, but I cannot reach it (using a browser) via the Elastic IP address Amazon assigned the box. Ping does not work either. I am trying to confirm it is reachable before I add the IP address to my own DNS entries.
-
1Are you sure you're using your elastic IP and not your private, could-local IP? – Feb 03 '12 at 16:34
-
@Robert - Hi, well the aws.*** address will not lookup via ping, (but works in the browser) so I am actually at a loss on how to find out. I tried ping and I tried a few internet sites that do a lookup. – Feb 03 '12 at 16:42
-
@Piotr - Yep. It's the "Elastic IP Address" not the Private IP Address. It also is used by Amazon in the header for the status tabs. – Feb 03 '12 at 16:43
-
Guido, does it have a public DNS and instance ID assigned? – Feb 03 '12 at 16:46
-
@Piotr - Yes. And the public DNS is reachable via a browser. Currently I am working behind a firewall, not sure if that will affect.....just attempted to ping a known site (msn.com) and that failed. Tethering my phone... – Guido Anselmi Feb 03 '12 at 17:12
-
@Piotr - Didn't help. The IP address is also embedded in the "Public DNS" entry. Not sure if Amazon doesn't allow direct IP addressing for some reason. – Guido Anselmi Feb 03 '12 at 17:21
-
Amazon definitely does allow direct IP access to your elastic IP. Have you actually tried to access you EC2 machine via its public IP (not the elastic IP)? – Piotr Justyna Feb 03 '12 at 17:26
-
@Piotr - The appear to be one in the same. (The public IP and the elastic IP) – Guido Anselmi Feb 03 '12 at 18:40
-
Ping is disabled by default in EC2 security groups. You need to allow ICMP echo and reply (see [here](http://serverfault.com/questions/318936/ec2-ping-and-security-settings/318938#318938)) for it to work. Also, are you able to SSH in (with the IP)? Try to map the IP to a DNS entry in your host file and see if it works - some web servers are setup to drop connections without a valid hostname (typically a 444 error). – cyberx86 Feb 03 '12 at 21:26
-
@cyberx86 - SSH works. Just connected. Which host file? – Guido Anselmi Feb 03 '12 at 21:46
-
SSH works means that the instance is accessible via its IP (since you used the IP). The host file on the computer you are connecting from (i.e. the computer with the browser). (You could also try to pass the public DNS as a host header and connect via the IP to try and deduce if it is a web server error - and of course, check your error logs). Also, what web server do you use and what error (the number, specifically) is returned when you try to go to the page via the IP? – cyberx86 Feb 03 '12 at 21:51
5 Answers
Things to check:
- Your elastic IP associated with your instance?
- Your security group of instance permits incoming connections?
- Your instance firewall permits incoming connections?
- Your application listens?
- 6,941
- 1
- 19
- 33
-
Was security group for me, thanks! They never mentioned this in any AWS tutorial. :( – emotality Aug 28 '16 at 21:35
-
1Other thing to check: try restarting EC2 instance. This did the trick for me (the elastic IP was associated with the instance while it was running). – nedned Feb 23 '17 at 04:27
-
-
I'm having the same issue as OP. I checked point 1, 2, 4 in the answer, also rebooted the EC2 instance. How do I check the 3rd point "Your instance firewall permits incoming connections"? Aren't incoming connections allowed by EC2 instance firewall? – Indominus Feb 24 '19 at 17:15
-
For me it was windows firewall settings AND security group settings. PING is enabled by the rather non intuitive 'File and Printer Sharing (Echo Request - ICMPv4-In' inbound rule. – Robbie Matthews May 24 '22 at 01:01
As others mentioned, the security group for your EC2 instance may not allow the HTTP port.
First,find the Security Group your instance is using.
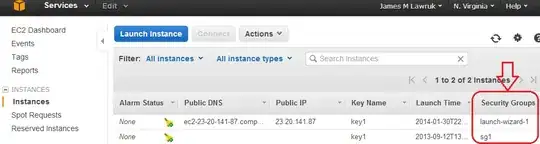
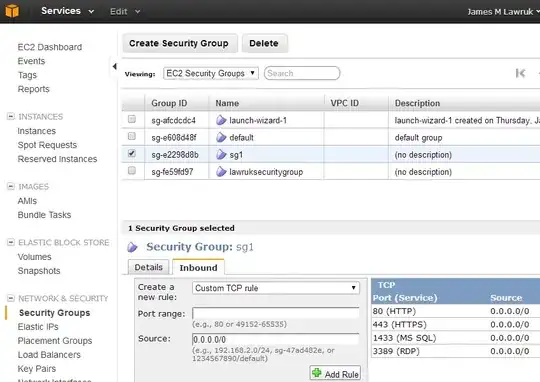
Then, under Network & Security, go to the Security Groups section. Select your instance's security group and add an Inbound Custom TCP rule for Port range 80.
- 617
- 2
- 9
- 18
-
2
-
2I`d rather accepted this answer, because AWS EC2 really creates instance without opened port 80 for TCP connections by default. – Arthur Kushman Jun 11 '15 at 13:13
-
Much better answer than Stone's answer. This (James') answer should be accepted as correct answer because it is an actual answer. Stone's respond is too generic ie. Things to check! – kannas Apr 07 '16 at 18:30
-
Worked for me.. I just add Custom TCP Rule with PORT : 80.. Thanks – Muhammad Azeem Jul 20 '16 at 14:40
-
Ohh, this was it! It has been driving me nuts for hours. I created a new Security Group with all the correct bindings. Checked firewall on the instance, checked if the web service is running or not and the VPC Security configs. But it turned out the Instance was using a whole different Security Group called "launch-wizard-1" !! – Zolbayar Jan 30 '19 at 03:40
Also make sure Route table of VPC is set to enable IP address outside the VPC (0.0.0.0/0) to flow from the subnet to the Internet gateway.
Navigate to VPC > Route Tables ; Route tab. Check Destination is 'mapped' to Target Internet Gateway Id (apart from local).
- 181
- 1
- 2
-
1Following the above instruction, I added a default route using the internet gateway as the target. To specify the default route put 0.0.0.0/0 as the destination. Once this was done I was able to reach my instance from the internet using it's public ip address – Peter Smallwood Nov 24 '18 at 10:30
-
It works for me. But I am curious that before I set up following this way, I already had another existing instance reachable from the Internet. Why cannot this time? – shintaroid Aug 23 '19 at 12:05
-
Saved my life! Was struggling with this issue for hours already. Thank you! – nnimis Apr 01 '20 at 01:10
Just adding this reply as it might help other EC2 Newbies. If the Public DNS for your EC2 instance is: Public DNS: ec2-46-137-53-149.eu-west-1.compute.amazonaws.com you can access the instance using the numeric portion of the DNS Address. In the above case http://46.137.53.149/
Obviously you will need to have the relevant TCP Port open in the security group/profile associated with your instance as mentioned above.
The private IP (e.g. 10.235.47.101) is not accessible from outside the AWS network and is only useful when you have a cluster of EC2 nodes and want faster communication between them.
- 211
- 2
- 3
Couple questions: what port are you trying to access? Do you have that port open on the security groups? Do you have an application listening on that port?
If I had to guess your security groups are not setup right. Make sure to open them to the correct ip addresses or to the world (0.0.0.0/0) if you are going access that port from multiple IPs.
If all that is not it, then dissociate and reallocate the IP to the instance.
- 335
- 1
- 3
- 8
-
@Chan-da-man- Yes ports are open and there is an app listening. Exact same URL except domain name swapped with IP. – Guido Anselmi Feb 03 '12 at 18:04
-
When you ping the full amazon cname does it come back with the elastic ip? – chantheman Feb 04 '12 at 17:50