I am fairly new to ESXi but have decided to dive into this, but have found out that things are not as easy as I had expected them to be (no doubt this is primarily caused by my lack of knowledge on the matter at this time).
What I have:
- A dedicated server with 1 NIC running ESXi
- A single (public) IP address for the host
- A set of (public) IP addresses intended for any use I see them fit. To keep things simple, let's imagine a single webserver for now.
What I want to achieve:
- Secure ESXi management; I really feel that a publicly accessible management host is wrong.
- I don't have any physical routers at my disposal so I cannot hide the host behind a physical VPN.
- Public access to some of my guest systems
- Additional guests need to sit on a private network.
- Public and private guests should optionally be able to communicate via the private network.
Currently, I'm a bit lost on how I should tackle this. I'd probably be able to get something running, but I don't want to start on the wrong basis or make choices that end up to be insecure.
Any help is appreciated.
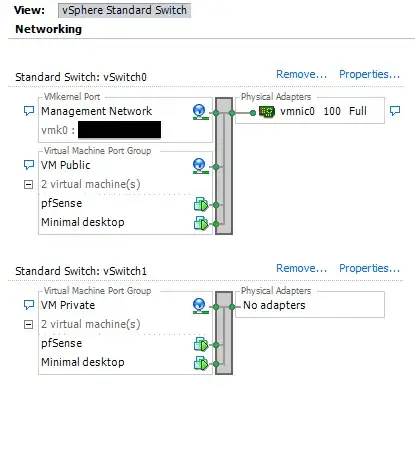
UPDATE: what I have achieved so far (and network screenshot):
- ESXi is up and running, still on the public interface
- I have configured a pfSense guest
- I have configured a DSL desktop to reach the pfSense guest through the private network.
I still feel that hiding ESXi behind a virtual VPN is quite risky, since I do not have console access. If I am overlooking something, or any alternatives are possible, I'd really like to know.