I've been able to set up TomatoUSB firmware with Ipredator via PPTP, the configuration is as follows:
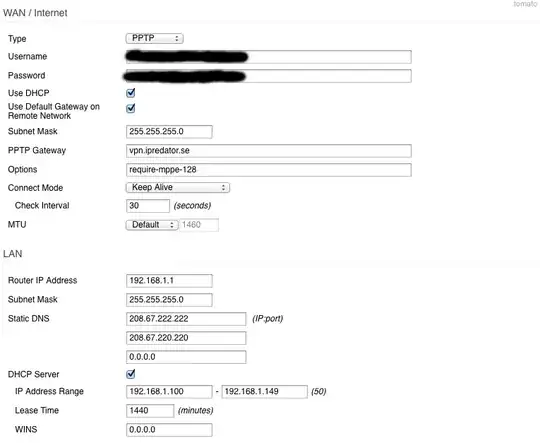
However, I don't want to use Ipredator PPTP VPN for every machine on my network, how to only use PPTP VPN for one MAC/IP?
Upon further investigation, I have the following iptables output:
root@unknown:/tmp/home/root# iptables -L
Chain INPUT (policy DROP)
target prot opt source destination
DROP all -- anywhere somehostname.vpn.ipredator.se
DROP all -- anywhere my.personal.isp.hostname.com
DROP all -- anywhere anywhere state INVALID
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
shlimit tcp -- anywhere anywhere tcp dpt:ssh state NEW
shlimit tcp -- anywhere anywhere tcp dpt:telnet state NEW
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
ACCEPT tcp -- anywhere unknown tcp dpt:ssh
Chain FORWARD (policy DROP)
target prot opt source destination
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere state INVALID
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN TCPMSS clamp to PMTU
restrict all -- anywhere anywhere
restrict all -- anywhere anywhere
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
wanin all -- anywhere anywhere
wanout all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
wanin all -- anywhere anywhere
wanout all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain rdev00 (1 references)
target prot opt source destination
DROP all -- anywhere anywhere MAC 00:19:C5:7B:84:89
Chain restrict (2 references)
target prot opt source destination
rdev00 all -- anywhere anywhere
Chain shlimit (2 references)
target prot opt source destination
all -- anywhere anywhere recent: SET name: shlimit side: source
DROP all -- anywhere anywhere recent: UPDATE seconds: 60 hit_count: 4 name: shlimit side: source
root@unknown:/tmp/home/root# ifconfig
br0 Link encap:Ethernet HWaddr 10:DF:21:DF:1B:C5
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:37083400 errors:0 dropped:0 overruns:0 frame:0
TX packets:36007047 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2111526714 (1.9 GiB) TX bytes:893920689 (852.5 MiB)
eth0 Link encap:Ethernet HWaddr 10:DF:20:CE:1B:B2
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:73849311 errors:0 dropped:0 overruns:0 frame:0
TX packets:71651191 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1860166371 (1.7 GiB) TX bytes:4061112643 (3.7 GiB)
Interrupt:4 Base address:0x2000
eth1 Link encap:Ethernet HWaddr 10:BF:20:DF:1A:B8
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:2167739 errors:1 dropped:0 overruns:0 frame:14874409
TX packets:2691377 errors:108 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1449581768 (1.3 GiB) TX bytes:2683796769 (2.4 GiB)
Interrupt:3 Base address:0x1000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MULTICAST MTU:16436 Metric:1
RX packets:1005 errors:0 dropped:0 overruns:0 frame:0
TX packets:1005 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:156929 (153.2 KiB) TX bytes:156929 (153.2 KiB)
ppp0 Link encap:Point-to-Point Protocol
inet addr:22.22.22.222 P-t-P:22.22.22.222 Mask:255.255.255.255
UP POINTOPOINT RUNNING MULTICAST MTU:1400 Metric:1
RX packets:1738332 errors:0 dropped:0 overruns:0 frame:0
TX packets:2089007 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:756439075 (721.3 MiB) TX bytes:1167050907 (1.0 GiB)
vlan1 Link encap:Ethernet HWaddr 20:CF:30:CE:0A:B6
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:36136587 errors:0 dropped:0 overruns:0 frame:0
TX packets:34736222 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2237528696 (2.0 GiB) TX bytes:4119244159 (3.8 GiB)
vlan2 Link encap:Ethernet HWaddr 10:BF:10:DE:1A:A7
inet addr:11.11.11.111 Bcast:11.11.11.111 Mask:255.255.254.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:37693742 errors:0 dropped:0 overruns:0 frame:0
TX packets:36914969 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2587444201 (2.4 GiB) TX bytes:4236835780 (3.9 GiB)
root@unknown:/tmp/home/root# ip route flush table 3
Nothing to flush.
root@unknown:/tmp/home/root# ip route add 192.168.1.0/24 dev br0 table 3
root@unknown:/tmp/home/root# ip route add 127.0.0.0/8 dev lo table 3
root@unknown:/tmp/home/root# ip route add default via 10.0.0.1 table 3
RTNETLINK answers: No such process
root@unknown:/tmp/home/root# ip rule add from 192.168.1.112 table 3
vlan2 has my actual ISP IP, I masked it to 11.11.11.111 for privacy reasons ppp0 has my actual PPTP IP, I masked it to 22.22.22.222 for privacy reasons
How can I only route certain machines via VPN?