My configuration includes: Cisco ACS as RADIUS server, MS AD, MS PKI, Cisco 2960G switches. Workstations are 95% XP Pro SP3 fully patched, some 7 pro fully patched.
Computer cert autoenrollment enabled and working.
GPO for 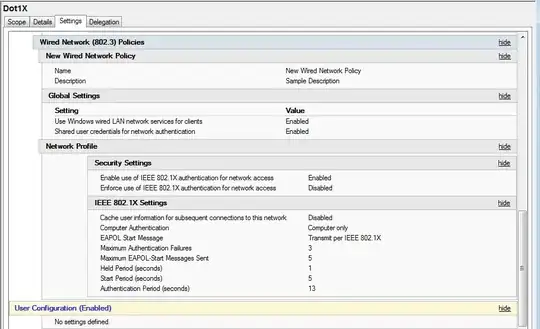
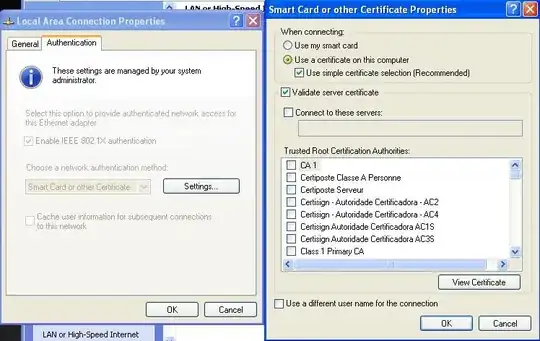
Resulting NIC settings from GPO on workstation:
Port configuration on the switches is as follows:
switchport access vlan 56
switchport mode access
authentication control-direction in
authentication event fail action authorize vlan 66
authentication event server dead action reinitialize vlan 56
authentication event no-response action authorize vlan 66
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication port-control auto
authentication violation protect
mab
dot1x pae authenticator
spanning-tree portfast
The problem I'm having is that as machines are booting up, they are attempting to authenticate with their hostname rather than certificate. This fails but then a minute later, they use the computer certificate and authentication is successful. The configuration is working (mostly) but every once in a while I get a computer (about 250 setup for dot1x so far) that tries to authenticate with its hostname which fails and then stops. If I restart the wired autoconfig service, it authenticates perfectly but rebooting re-creates the problem.
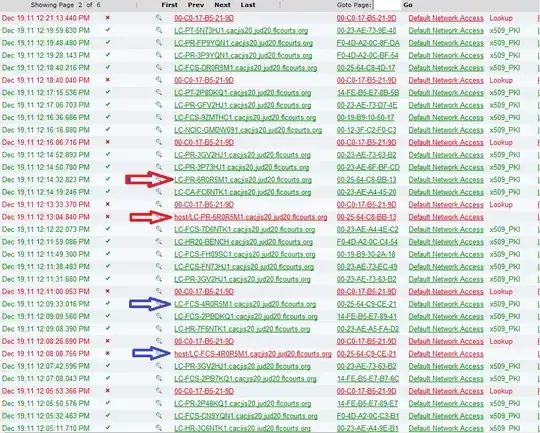
It is also very annoying that these errors show up in the logs because the frequency of them prevents me from setting up alerts to notify me when an actual unauthorized computer has been connected to the network. i.e. too many false positives.
My question is why does the workstation attempt to authenticate with its hostname first when I have configured it to use its computer certificate?
On the wireless side, everything is working perfectly. Cisco AP's and WLCs.
EDIT* I found a hotfix KB957931 that indicates that XP SP3 will ignore dot1x traffic for 20 minutes after receiving an authentication failure message. The hotfix allows you to create a registry key to modify this previously hard-coded setting. I applied the patch to a workstation and changed the blocktime to 1 minute (the minimum) and now, after a minute the workstation does authenticate but does not renew its IP. The one minute wait is not ideal nor is dealing with renewing the IP so I am still good with the original question which is why does the box choose to identify itself with its name instead of its certificate?
UPDATE* 1/11/12 I ran into this problem again today and poked around the client some. I noticed that in the authentication tab on the local area network connection, the settings were no longer grayed out and were changed to use passwords rather than certificates. I know local group policy is applied at boot up no matter if the PC belongs to a domain or not and I know that my domain GPO overrides whatever is set locally. When the PC fails to authenticate for some reason (power failure of network gear in this case) it no longer applies the domain policies and apparently my settings all get changed. I'm not sure why they are changing since no local GPO's were ever configured.
So, in addition to wanting to know why PC's identify themselves with their hostname before using their certificate I now have a second question.
How do I create a local group policy on XP workstations with the dot1x settings (they are missing from the default templates available) and how can I push those out to all my workstations? I've looked into using security templates but they do not contain the settings I need. I need to apply settings from Computer Config -> Policies -> Windows Settings -> Security Settings -> System Services. That last bit is missing from both local GPO's on XP and also from the SCA snap-in.
It should be noted that I already have a domain GPO that works perfectly. Isn't there an easy way to export this and apply it as the local GPO for each workstation?
Full points will be rewarded for an answer to either question.