I've just tried logging into a Fedora (release 13 Goddard) server using SSH (PuTTY, Windows). For some reason the Enter after typing my username didn't go through and I typed in my password and hit Enter again. I only realized my mistake when the server greeted me with a happy
myusername MYPASSWORD@server.example.com's password:
I broke off the connection at this point and changed my password on that machine (through a separate SSH connection).
... now my question is: Is such a failed login stored in plain text in any logfile? In other words, have I just forced my (now-outdated) password in front of the eyes of the remote admin the next time he scans his logs?
Update
Thanks for all the comments about the implied question "what to do to prevent this in the future". For quick, one-off connections I'll use this PuTTY feature now:
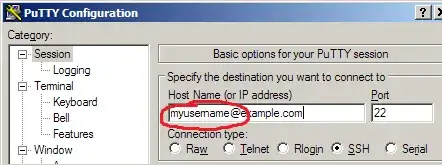
to replace the where-was-it-again "auto-login username" option
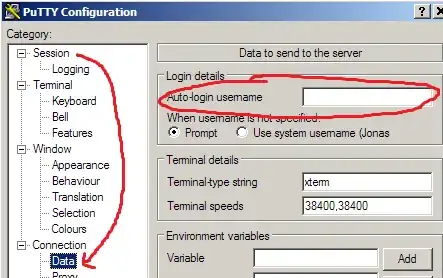
I'll also start using ssh keys more often, as explained in the PuTTY docs.