I have an issue where websites that are hosted on a web server (www.example.com) are not accessible from their own network when accessed via its public IP address, but they are accessible from every other network.
This is the network setup:
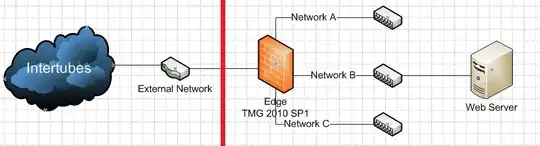
I have a TMG 2010 SP1 machine behind a router that's managed by someone else (that I have no access to), and behind that router is the internet.
The "external network" router has a 1:1 NAT for IP addresses pointing to corresponding private IP addresses on the TMG box. The TMG Edge then has a web proxy rule that forwards the requests (to www.example.com) to a web server on Network B.
When you try to access www.example.com (that is hosted on Network B) via its public IP address, the following happens:
Internet - HTTP 200 OK External - HTTP 200 OK Network A - HTTP 200 OK Network B - Error Code 10060: Connection timeout Network C - HTTP 200 OK
I see the traffic hit the TMG firewall, but then it seems to get lost. It does not forward the packet to the external network (which, if it did, it would send straight back). Wireshark shows the packet coming in on the Network B interface, but it never leaves the TMG.
After requesting http://www.example.com/ The TMG firewall log shows an initial permitted outbound request, followed 60 seconds later by:
- Failed Connection Attempt
- Source Network: Network B
- Destination Network: External
- URL: http://203.206.238.xxx (the public IP address, not the URL I actually requested)
Status: 10060 A connection attempt failed because the connected party did not properly respond after a period of time, or established connection failed because connected host has failed to respond.
I have no idea where the problem lies. I don't know if it's because for some reason it's proxying the public IP address as the URL (there is proxy rules for the IP address, only for FQDNs), or if it's something completely else.