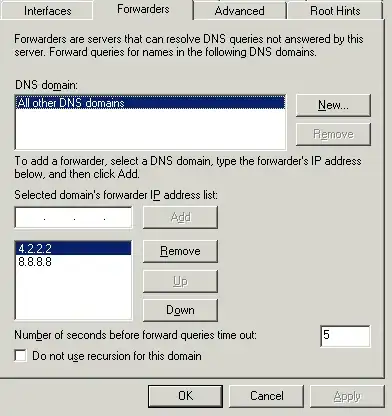
We have an 2K3 R2 AD server. It is also serves as our DNS server.
When I look at the DNS entries I see the following:
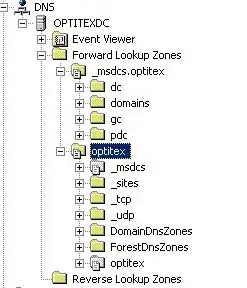
do I really need all these entries?
I currently have a problem that my AD can not access the internet. From SF-Q I can guess it has to do with my dns entries, and I think that fixing that will solve my network access.
Running NetDiag /l shows me an error in the DNS entry as follow
DNS test . . . . . . . . . . . . . : Failed
[WARNING] Cannot find a primary authoritative DNS server for the name
'OptiTexDC.optitex.'. [ERROR_TIMEOUT]
The name 'OptiTexDC.optitex.' may not be registered in DNS.
[WARNING] The DNS entries for this DC are not registered correctly on DNS server '192.168.0.2'. Please wait for 30 minutes for DNS server replication.
[WARNING] The DNS entries for this DC cannot be verified right now on DNS server 80.179.52.100, ERROR_TIMEOUT.
[FATAL] No DNS servers have the DNS records for this DC registered.
I want to point, all of my users/computers et el. can access the internet.
I am not really sure what to do?!
<< edit >>
DNS management forwaders are defined as my ISP provider gave me. This usually propogates to all users.
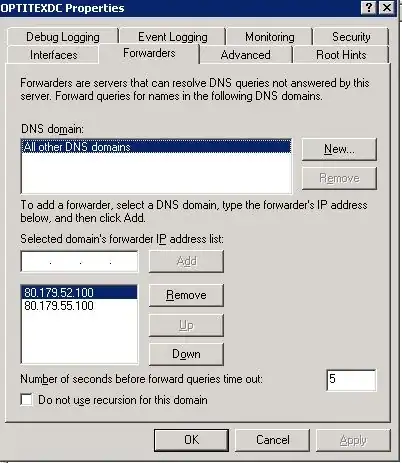 Should I add my DC (192.168.0.2) as one as well?
Should I add my DC (192.168.0.2) as one as well?
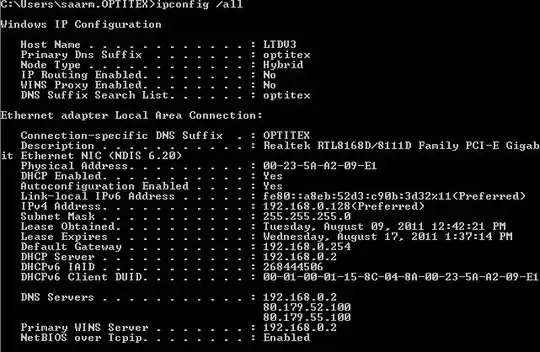
This is a ipcnofig /all from a client. Both my ISP DNS are listed, as well as my Domain.
Adding some more information: Looking at the Server Event viewer, Under DNS, I see the following:
Event Type: Warning
Event Source: DNS
Event Category: None
Event ID: 7062
Date: 8/10/2011
Time: 16:03:03
User: N/A
Computer: OPTITEXDC
Description:
The DNS server encountered a packet addressed to itself on IP address 192.168.0.2. The packet is for the DNS name "localhost.OPTITEX.OPTITEX.". The packet will be discarded. This condition usually indicates a configuration error.
Check the following areas for possible self-send configuration errors:
1) Forwarders list. (DNS servers should not forward to themselves).
2) Master lists of secondary zones.
3) Notify lists of primary zones.
4) Delegations of subzones. Must not contain NS record for this DNS server unless subzone is also on this server.
5) Root hints.
Example of self-delegation:
-> This DNS server dns1.example.microsoft.com is the primary for the zone example.microsoft.com.
-> The example.microsoft.com zone contains a delegation of bar.example.microsoft.com to dns1.example.microsoft.com,
(bar.example.microsoft.com NS dns1.example.microsoft.com)
-> BUT the bar.example.microsoft.com zone is NOT on this server.
Note, you should make this delegation check (with nslookup or DNS manager) both on this DNS server and on the server(s) you delegated the subzone to. It is possible that the delegation was done correctly, but that the primary DNS for the subzone, has any incorrect NS record pointing back at this server. If this incorrect NS record is cached at this server, then the self-send could result. If found, the subzone DNS server admin should remove the offending NS record.
You can use the DNS server debug logging facility to track down the cause of this problem.
For more information, see Help and Support Center at http://go.microsoft.com/fwlink/events.asp.
Data: 0000: 50 25 00 00 P%..
- I visited the link provided. Did not help me.
<< edit - Add Server connection settings >>
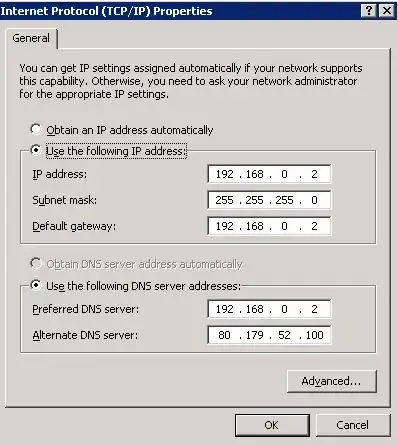
I am also adding my server network settings. I don't think I can make these settings dynamically from DHCP as I am the DHCP. I do have set as a DNS - my own IP, and 1 of my ISP's. Do I need to change?
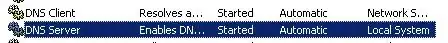
Checklist:
Both DNS Client and DNS Server are working on the server.
Thanks