Trying to configure my first Juniper firewall, an SSG5 (running 6.2.0r11.0), but having some trouble with the vlans. I haven't found much documentation relating to what I'm trying to do; possibly because it's not possible, or perhaps I'm just looking in the wrong places.
Here's a diagram of the setup I'm trying to achieve:
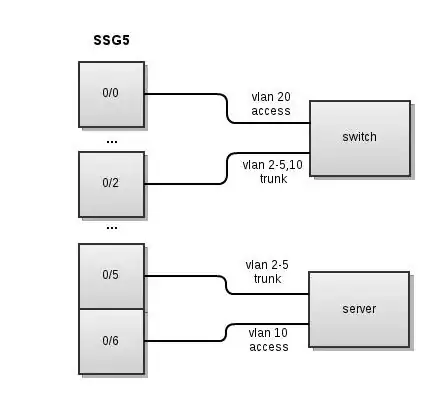
My first question - is this possible with the Juniper SSG5?
If so, I'm wondering if someone can give me some hints on how to set it up. The switch (Cisco 3550) is configured and working properly, and so far I've:
- Created zones for each vlan
- Set up sub-interfaces on 0/2 and 0/5; one for each vlan
- Put each sub-interface into their respective zone
- Put 0/6 into the zone for vlan 10
I have a machine connected to the switch using vlan 10 (access port) and it can ping the 0/2 sub-interface for vlan 10. However, it can't ping the physical interface 0/6 or the host connected to 0/6. I've also tried creating a sub-interface on 0/6 for vlan 10 (putting it in the vlan 10 zone), but it can't ping that sub-interface either (ping enabled on all interfaces and sub-interfaces).
Thanks in advance.