Can anyone recommend a fail2ban-like tool for a Windows OS? I've got a couple of Windows Media servers that get hammered with brute force authentication attempts. I would like to plug these authentication failures into some kind of blocking tool.
-
Could you provide some clarification? What are you trying to accomplish? What version of Windows? Are you trying to block bad logins to PCs, network shares, Terminal Servers, IIS-hosted pages, etc? – Skawt Jun 18 '09 at 06:20
-
Clarified my question. – nurikabe Jun 18 '09 at 09:45
9 Answers
I know of no tool that will do this "out of the box". I wrote a script to do something like this with failed OpenSSH logons on Windows, but I can't share it with you because it "belongs" to the Customer for whom I wrote it.
Having said that, it was a simple VBScript program that had an event log sink to watch for new failed logons and, if enough happened in a time window, add an IP route (using the "route" command) to route traffic to the offending IP address to a "MS Loopback Adapter" on the system.
For other types of logs, it would be a fairly trivial matter to write. Since I didn't have IPtables on Windows, the loopback adapter seemed like the next best thing. (You can't do a "route x.x.x.x mask 255.255.255.255 127.0.0.1" on Windows-- you need an adapter to route the traffic to, because the 127.0.0.1 loopback isn't a "real" interface on Windows.)
(If you want something like this written, contact me out-of-band and we can discuss the specifics of such an arrangement.)
Edit:
I decided to write something to do this and I've released it under a Free license.
- 141,071
- 19
- 191
- 328
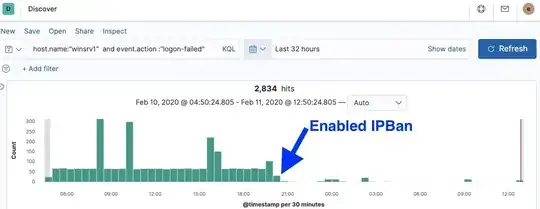
I recently installed IPBan on Windows Server 2019:
https://github.com/digitalruby/ipban
- 189
- 1
- 1
- 7
-
-
1@Kreker, that's Discover app in the Kibana. The data is sent by Winlogbeat. – Slavik Feb 11 '21 at 08:02
-
What's EvlWatcher?
It's basically a fail2ban for windows. Its goals are also mainly what we love about fail2ban:
pre-configured
no-initial-fucking-around-with-scripts-or-config-files
install-and-forget
- 365
- 3
- 8
Check out this project - ts_block
I'm using it and thus far its terrific (Windows Server 2008 R2 RDS, system is behind a firewall but I didn't feel like using an ssl vpn gateway to the server)
- 19,532
- 4
- 55
- 75
- 39
- 1
I found a tool called RdpGuard (https://rdpguard.com) that starts at $79 and appears like it might work. I haven't tested it yet, but might give it a go for my SMTP solution.
- 11
- 1
-
1It would probably be a good idea to have used the product, before you make the recommendation. – Cory Knutson Jul 14 '17 at 19:35
-
A VM hosting company I started using includes a copy on their Windows VMs. It does the trick, and there are hundreds of firewall entries after just a few weeks. – atmarx Jan 08 '19 at 12:05
-
I've been using this lately and it works extremely well. I recommend it. I love how it's an easy install with a GUI interface. There are no scripts to set up and run. It's all-inclusive and allows a lot of auto-blocking beyond just RDP, such as SMTP, MySQL, MS SQL, and more if there are failed logins. Very configurable. I have no affiliation with the company that makes this program, just FYI. – Ethan Allen Feb 20 '20 at 20:47
-
You may check Win2ban which is a Fail2ban implementation for Windows systems. It is a packaging of Fail2ban, Python, Cygwin, Winlogbeat and many other related tools to make it a complete and ready-to-use solution for brute-force attack protection. A full functional free edition is available for non-commercial use.
NB! We are the developer of the solution.
- 111
- 1
- 5
It doesn't look like fail2ban runs on windows at all, as it requires iptables which is only available on Linux.
However, I would suggest that you block everything and white-list only the IPs/names you want to be able to connect to the server(s) in question, if at all possible.
- 1,499
- 2
- 13
- 25