We're reviewing Wireshark captures from a few client machines that are showing multiple duplicate ACK records which then triggers retransmit and out-of-sequence packets.
These are shown in the following screen shot. .26 is client and .252 is server.
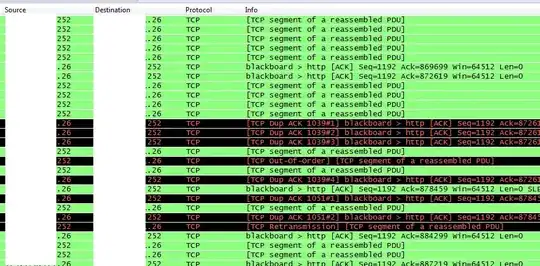
What causes the duplicate ACK records?
More background if it helps:
We're investigating network throughput concerns at one particular client site. The perceived issue from a user interface perspective is that data is being transmitted slowly despite an underutilized 1gbps WAN connection.
Almost all of the client machines have the same issue, tested at more than 20 machines. We did find two machines that do not have the problem. We're in the process of identifying what is different in their configuration. We did notice that in the two machines that do not have the problem, we only ever saw at most one duplicate ACK record. The machines that have the problem usually have three duplicate ACK records. One notable difference is that the machines that work fine all belong to members of the network operations team and all of other machines are for "regular" employees. The machines are supposed to be standard but the network admins could have made changes on their local systems, which is another aspect we're researching.
We tried changing the TcpMaxDupAcks setting on the server but the value we really need is 5 and the valid range is only 1-3.
Server is Windows Server 2003. Clients are all enterprise managed Windows XP. All clients, including the two working ones, have Symantec anti-virus installed.
This is the only client site out of hundreds that has exhibited this problem.
pathping shows 56ms RTT and consistent 0/100 packet loss even from the problem machines.
Thanks,
Sam