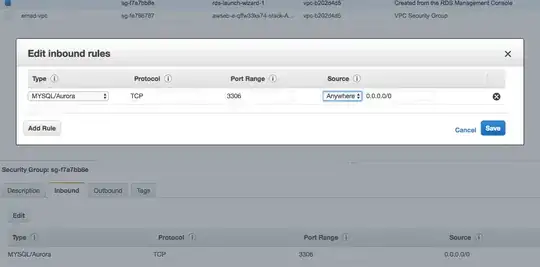
So, I just created the Amazon RDS account. And I started an instance of database.
The "endpoint" is:
abcw3n-prod.cbmbuiv8aakk.us-east-1.rds.amazonaws.com
Great! Now I try to connect to it from one of my other EC2 instances.
mysql -uUSER -pPASS -habcw3n-prod.cbmbuiv8aakk.us-east-1.rds.amazonaws.com
But nothing works and it just hangs.
I tried to ping it, and nothing works either. Nothing happens.
Do I need to change some settings?