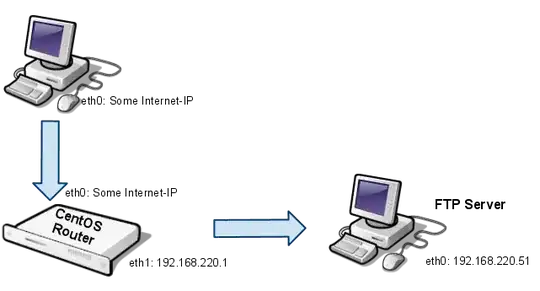
I'm trying to forward an FTP-server with IPTables. The FTP-Server is running on a Windows 2008 box (Cerberus).
Details Win Box:
- IP: 192.168.220.51
- FTP-Port: 21
- PASV-Ports: 11000-13000
The FTP-server works great in LAN.
The router is working fine for other clients (Serving NAT, DHCP, Firewall,...). I need to forward the FTP-service to the outside world, but I can't use ports 20-21 (already taken).
I tried this, but it didn't work:
iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 2121 -j DNAT --to 192.168.220.51:21
Current IPTables config:
[root@router ~]# service iptables status
Table: nat
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
2 MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Table: filter
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT all -- 127.0.0.1 0.0.0.0/0
2 DROP all -- 0.0.0.0/0 0.0.0.0/0
3 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:2222
4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:67
5 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:68
6 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194
7 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080
8 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
9 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3128
10 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:53
11 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:53
12 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
13 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
14 DROP udp -- 0.0.0.0/0 0.0.0.0/0
15 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Any help would be great :-).
Bounty-Edit: I have not been able to figure this out, any help would be greatly appreciated.
EDIT2
I'm able to telnet into my FTP-server now, after running there commands:
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 2121 -j DNAT --to 192.168.220.51:21
I'm starting to get there... I think I just need to get my PASV-Ports working now...
EDIT3: Extra Info
[root@router ~]# iptables -L -n -v
Chain INPUT (policy ACCEPT 3251 packets, 154K bytes)
pkts bytes target prot opt in out source destination
540 48534 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0
4270K 5625M ACCEPT all -- * * 192.168.220.0/24 0.0.0.0/0
0 0 DROP all -- eth1 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:2222
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:67
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:68
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194
65 8487 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
8 404 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3128
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
63870 81M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
974 224K DROP udp -- * * 0.0.0.0/0 0.0.0.0/0
638 34956 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02
Chain FORWARD (policy ACCEPT 3578K packets, 3355M bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 2275K packets, 703M bytes)
pkts bytes target prot opt in out source destination
[root@router ~]# iptables -L -n -v -t nat
Chain PREROUTING (policy ACCEPT 33954 packets, 2595K bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- eth0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:2121 to:192.168.220.51:21
Chain POSTROUTING (policy ACCEPT 5925 packets, 699K bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * eth1 0.0.0.0/0 0.0.0.0/0
27170 1785K MASQUERADE all -- * eth0 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 5777 packets, 457K bytes)
pkts bytes target prot opt in out source destination
Solution
This is how I did it, might not be very pretty, but it works.
[root@router ~]# iptables -t nat -I PREROUTING -p tcp --dport 2121 -j DNAT --to 192.168.220.51:2121
[root@router ~]# iptables -I FORWARD -p tcp -d 192.168.220.51 --dport 2121 -j ACCEPT
[root@router ~]# iptables -t nat -I PREROUTING -p tcp --dport 11000:13000 -j DNAT --to 192.168.220.51:11000-13000
[root@router ~]# iptables -I FORWARD -p tcp -d 192.168.220.51 --dport 11000:13000 -j ACCEPT
Some extra notes: The FTP-server is listening on bot 21 an 2121 and the PASV-range is set from 11000 to 13000