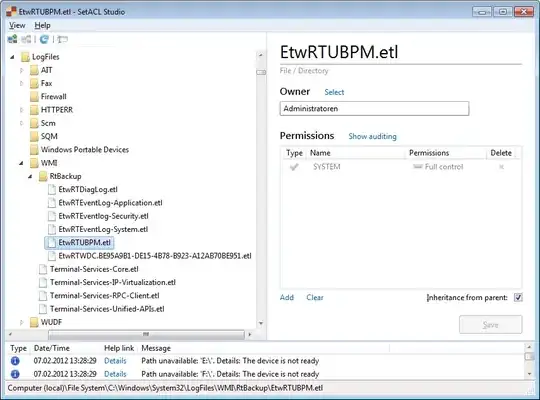
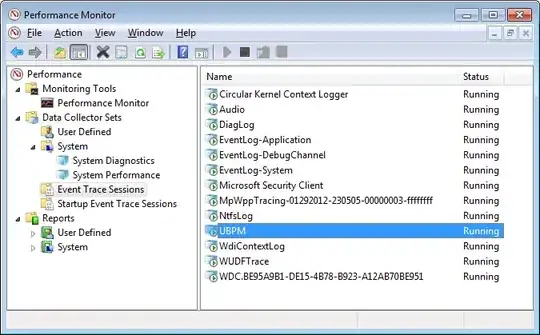
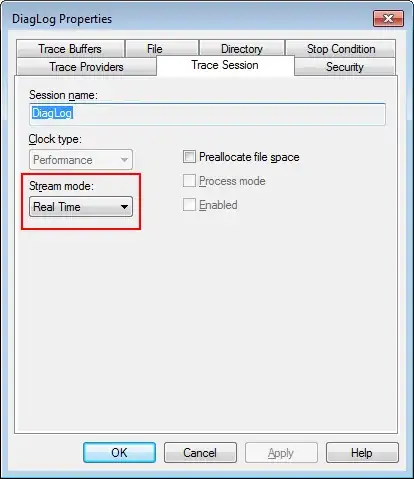
I occasionally notice in Resource Monitor hard disk activity related to ETL files in the folder C:\Windows\System32\LogFiles\WMI\RtBackup.
Which process/service creates these ETL files and what is their purpose?
Resource Monitor shows "System" as the process which is correct since ETW traces (that is what ETL files are) are created by the kernel. But I am interested in the process that causes the traces to be created.
This happens on Windows 7, by the way.