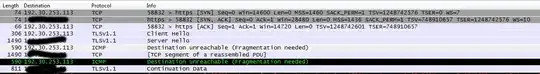
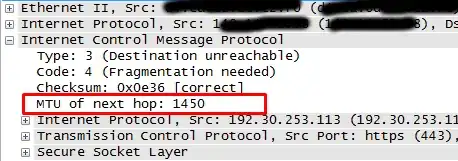
I've run into a problem on my Debian VPS (a xen domU) regarding SSL. Namely almost all SSL connections hangs at client hello. For example:
# curl -vI https://graph.facebook.com
- About to connect() to graph.facebook.com port 443 (#0)
- Trying 66.220.146.48... connected
- Connected to graph.facebook.com (66.220.146.48) port 443 (#0)
- successfully set certificate verify locations:
- CAfile: none CApath: /etc/ssl/certs
- SSLv3, TLS handshake, Client hello (1):
It's the same when using the openssl client. However, some of the SSL traffic works (for example https://www.nordea.se).
Server
#uname -a
Linux server.com 2.6.26-1-xen-amd64 #1 SMP Fri Mar 13 21:39:38 UTC 2009 x86_64 GNU/Linux
It does however work on my Dom 0 (the main xen host).
Apt-get
I can't even run apt-get update with the debian security sources (hangs on reading headers)
Open SSL
At the begining I thought I had an old openssl client (0.9.8o-4) since I appeared to have a newer on the Dom 0 (0.9.8g-15+lenny8) but doing a manuanl update on the openssl deb didn't help.
Open SSL Client
This is the full output of when the openssl client hangs: http://pastebin.com/PAjwMap9
Closing thoughts
I've Googled the crap out of this, and I'm not getting any further. I've seen problems with curl, apt-get etc. but they are all specific relating to the very application - not general for the system. Any thoughts?