I've got a problem getting Windows Authentication (Kerberos) to work when passing credentials from the user, to IIS then from IIS to SQL. I have setup SPN's for SQL, and set the IIS server account up to allow delegation.
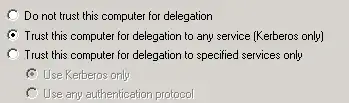
If I set the IIS computer account to allow Delegation for any service, it works:
However if I set it up for specific services, the credentials are not passed and I get an error about connecting with the anonymous user:
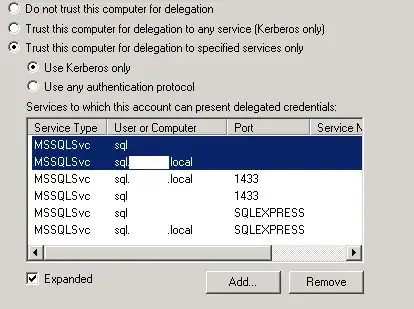
As you can see, I'm connecting to SQL Express Instance, and I've set up a number of SPN's to try and resolve this, no luck with any of them. Obviously the fact that it works when allowing any service, says to me that something else is missing from this list of services, but I don't know what!