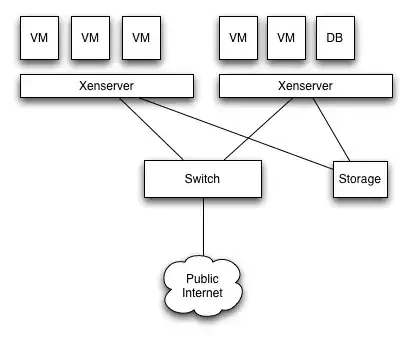
I'd have a network like this currently. Basically, It's two Xenservers connected to our colocation provider's switch via one ethernet cable per server. Each server currently has a second ethernet card which storage is attached to (iSCSI). Each of the VMs (and Xen hosts) have a public IP. All the VMs communicate with each other via their public IP.
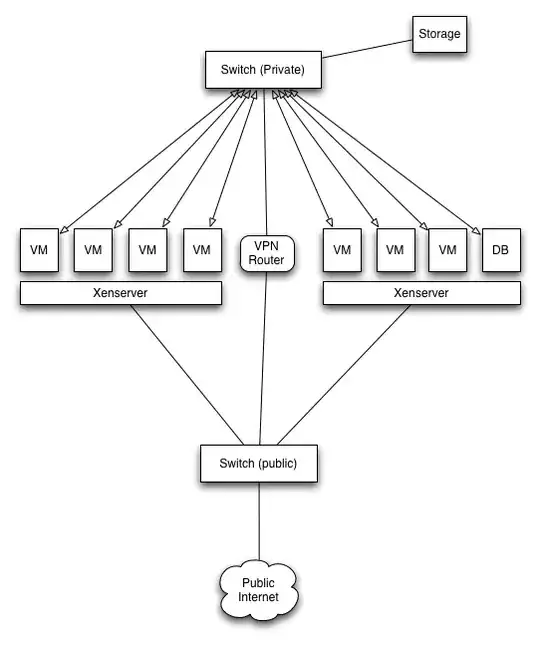
What I'd like to setup is a situation like this where each VM has at least a private address and only public facing servers would have a public IP. As well, storage would be connected to the switch instead of directly attached. As the private network would be inaccessible to the outside world, I'd like VPN so I can connect to and administer the private network.
That said I don't know very much about networking (in terms of setting this all up)
So the questions are:
1) How do I virtually network multiple VMs (on seperate hosts) together (for the private network)?
2) How do I set up virtual networking in Xen center?
3) would it be preferable to get a switch that supports VLaning and segment the network that way?
I'd be grateful to hear any advice the community has on these matters. Thanks in advance.