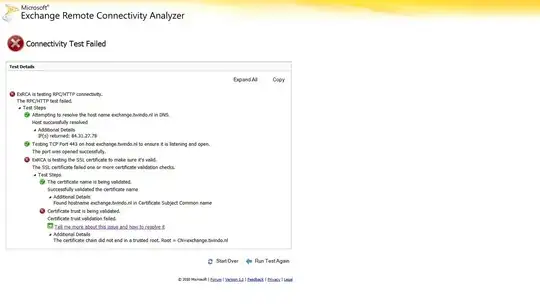
Sounds like a little Public Key Infrastructure (PKI) information is needed here.
When you create a self-signed certificate, it just says "I am a valid cert, nobody trusts me."
When you get a certificate signed by, say, GoDaddy, the cert then says "I am a valid cert, GoDaddy trusts me". The signer here is called a Certificate Authority (CA)
Your browser has a list of certs that says "I trust these CAs to sign certificates", and one of those is GoDaddy. So, if I trust GoDaddy, and GoDaddy trusts you, then I trust you. However, as a webbrowser, I don't trust just anybody, just this list of CAs.
However, this list can be modified. If you set up your own CA (you trust it), and use that CA to sign a cert, then the cert says "I'm a valid cert, MyCA trusts me". Then you can add your CA to the webbrowser, so it says "I trust MyCA, MyCA vouches for this site, so everything is cool now."