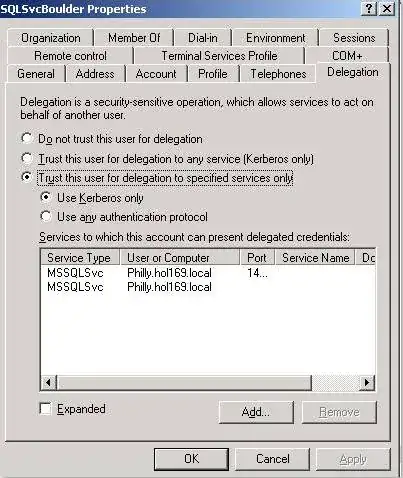
All my nerdly life, I've dealt with this limitation of Windows Domains
- Login - console
- Integrated auth to something (usually web app)
- My credentials can't move to another server (e.g. database or file system). They have to trust machine 2.
Is there a configuration that changes this behavior? In many many cases, 3 hops would be amazingly convenient.
What is the specific reason that credentials should not delegate twice (client->server->server)?