I need to tunnel my SSH server through an HTTPS port using thttpd (I can change to lighttpd if necessary, but I'm trying to avoid installing Apache since it's an underpowered box). I haven't been able to find anything that confirms or denies this ability of thttpd.
5 Answers
If it has a TCP/IP Listening port you can set up an SSH Tunnel to it. You may want to check to see if the port is already in use on your client system first. You can do this with the netstat command On Windows you can run
# netstat -ano
on Linux
# netstat -anut |grep LISTEN
SSH Tunneling can be a little bit difficult to get your head around. With all the diagrams and examples online even I get confused and I use tunnels on a daily basis. I find it best to think about it like this: Your SSH client opens a connection to a server and redirects ports from that network to your *client system creating a listening port for each redirect on your *client system.
-*- The client system is the system you are using the SSH client which may also be referred to as your local system
Sounds like you would like an example of an HTTPS port 443 tunnel!
From a Windows Client System
This example will use the "Putty" client for Windows which can be found on the Putty download site here We'll assume you are running the HTTPS on port 443 on the same system you are running your SSH server. We'll use the Localhost IP address of 127.0.0.1 (127.0.0.1 will always return the system you are logged onto)
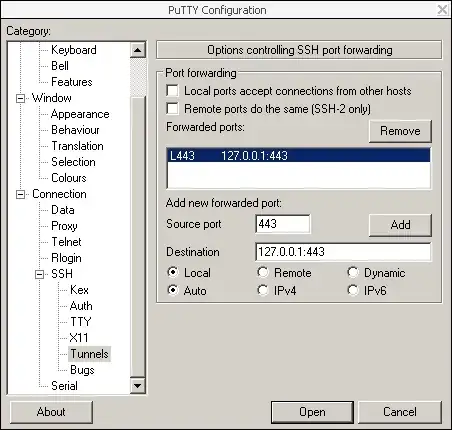
From your Putty Window navigate the left column "category" options menu. Expand the "Connection" > "SSH" > "Tunnels" menu. In the "Source port" text field enter 443, in the "Destination" text field enter 127.0.0.1:443 then click the Add button. The "Forwarded Ports" text area will now show "L443 127.0.0.1:443"
(source: hilands.com)
From a Linux Terminal
This should work I didn't test it though....
# ssh -L 443:127.0.0.1:443 <sshuser>@<sshserver ip>
But my SSH server resides on a different Server than my HTTPS Server!
Thats easy replace 127.0.0.1 in the above examples to the IP address your SSH server uses to connect to the HTTPS server!
Gotcha
After configuring the ssh tunnel you can now open the browser on your client machine. Instead of going to the normal IP address port 443 you will use 127.0.0.1 in your local browser.
https://127.0.0.1
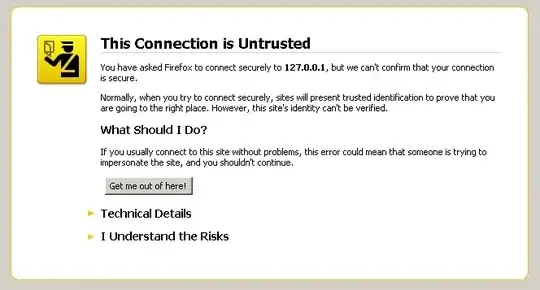
Doing this may upset your SSL certificate. In Firefox you will receive the following error message:
(source: hilands.com)
Continue through the prompts and allow your cert.
- 1,213
- 3
- 15
- 22
- 41
- 2
Have you tried it? If not, why not? Why ask a question here if something works when you haven't even tried it? As long as you're only talking about using port 443 to get past some firewalls and not truly tunneling over HTTPS then it should work fine (it's not really clear from your question, you mention both).
- 720
- 2
- 8
- 18
-
I've tried setting the port to 443 and using it like that, but the firewall ends up blocking it. I'll need to actually tunnel it using HTTPS, but nothing in the documentation for thttpd says how to do this. – May 11 '10 at 17:55
-
Port 443 == HTTPS If you are trying to make SSH traffic appear to be HTTPS activity that is a whole other ball game. – David Rickman Jun 18 '10 at 18:16
I don't know thttpd at all. I barely know lighttpd either.
But if they can serve HTTPS, you could use a tool like SSL Explorer. It can do a lot more than give you SSH access to your network.
Otherwise, these tools may help you :
- stunnel
- corkscrew
- proxytunnel
Some even work with classic HTTP (no need for SSL/TLS).
- 1,962
- 2
- 17
- 25
Although Putty would work fine, I would recommend a different option: You can create a nice tunnel (on port 443 obviously and not technically https but maybe good enough) using WinSSHD and Tunnelier as a client.
- 4,172
- 10
- 45
- 59