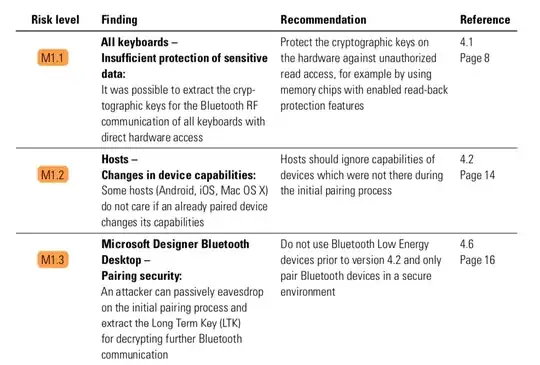
Since most of the answers are 10 years old as of today here are the 2018 results of some german security researches on the topic. They claim that modern BT keyboards have their most critical weakness when an attacker manages to get physical access to the device and extracts the crypto keys or is able to eavesdrop during the pairing process.
Here is their paper: https://www.syss.de/fileadmin/dokumente/Publikationen/2018/Security_of_Modern_Bluetooth_Keyboards.pdf
Their summary:
During this research project with a total duration of 15 person-days,
SySS GmbH could identify some security issues concerning the three
tested Bluetooth keyboards.
The secret pairing information stored on the keyboards can be easily
extracted by an attacker with physical access. The credentials in this
information can be used to conduct further attacks on the host.
The 1byone keyboard does not require authentication when pairing to a
Windows 10 host and the communication of the Microsoft Designer
Bluetooth keyboard can be decrypted if an attacker passively
eavesdrops on the pairing process.
Furthermore, by continuously sending pairing requests to some
operating systems, an attacker can prevent other devices from pairing
(denial-of-service).
And here are their key findings: