How do you grant access to network resources to the LocalSystem (NT AUTHORITY\SYSTEM) account?
Background
When accessing the network, the LocalSystem account acts as the computer on the network:
LocalSystem Account
The LocalSystem account is a predefined local account used by the service control manager.
...and acts as the computer on the network.
Or to say the same thing again: The LocalSystem account acts as the computer on the network:
When a service runs under the LocalSystem account on a computer that is a domain member, the service has whatever network access is granted to the computer account, or to any groups of which the computer account is a member.
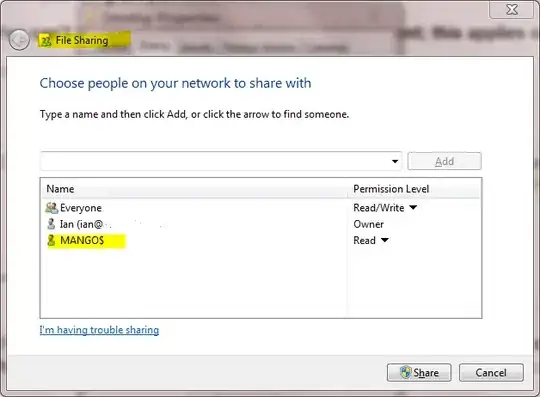
How does one grant a "computer" access to a shared folder and files?
Note:
Computer accounts typically have few privileges and do not belong to groups.
So how would i grant a computer access to one of my shares; considering that "Everyone" already has access?
Note: workgroup
| Account | Presents credentials |
|----------------|----------------------|
| LocalSystem | Machine$ |
| LocalService | Anonymous |
| NetworkService | Machine$ |