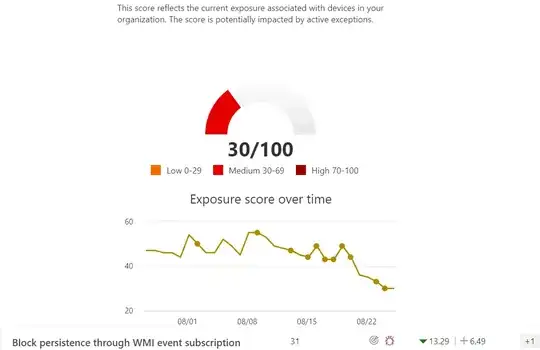
I am trying to improve our exposure score on Microsoft Defender and noted that "Block persistence through WMI event subscription" has a remediation which Ive already applied since almost a month now.
Remediation:
Ensure that Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. (checked and applied given the 0 exposed devices, and 0 impact)
Enable this ASR rule in Block mode using Group Policy (done)
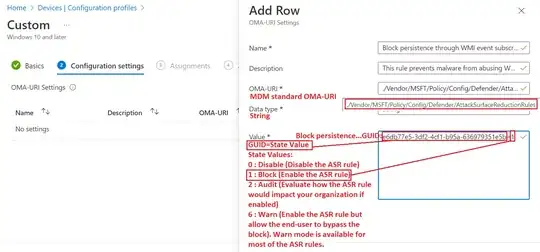
However, despite the attack surface reduction rule blocking persistence through WMI event subscriptions as reported on MEM (endpoint manager/intune),
it just doesnt seem to be really syncing with the remediation on Microsoft defender. The impact appears to have remained the same, and even my PC, despite the latest updates, appears to still reflect as an exposed device.