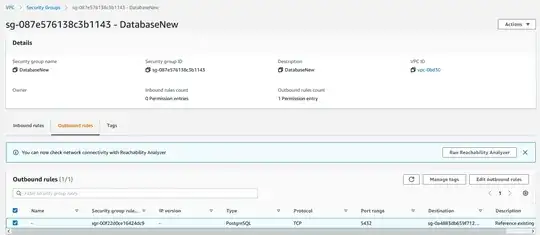
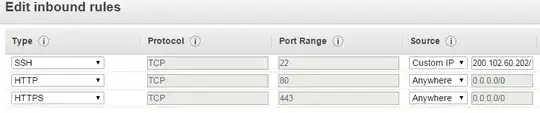
I have an existing prod Postgres database and I would like to replicate a table to a new Postgres database. In order to get the two to be able to talk to each other, I had to edit an AWS security group and add the public IP address of the new database since both databases are on a common VPC. While reading, I saw that the public IP of an RDS database can change. This would mean that the IP entered into the security group is no longer valid.
Is there a way to add my new database into the security group without being impacted by IP address changes?