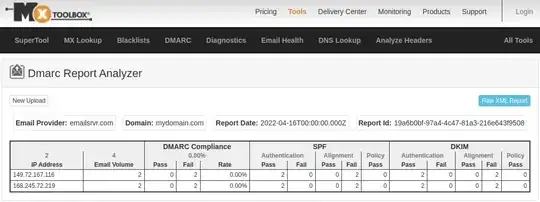
Pretty new to spf/dkim and dmark.
After setting this up just this morning I already got a report on a new website. Our service eamils our users via sendgrid and the rest of the emails are sent from our google workspace accounts.
Our SPF looks like the following:
v=spf1 include:_spf.google.com include:sendgrid.net ~all
Google is authenticing the DKIM records, based on their control panel, I can only "stop authenticating" (How long should it take for google to authenticate a DKIM TXT DNS entry?)
The dmarc dns record looks like:
v=DMARC1; p=none; rua=mailto:noreply-dmarc-support@mydomain.com; ruf=mailto:noreply-dmarc-support@mydomain.com; fo=0;
So based on this I'm not sure if the screenshot report is saying I have things configured wrong, or if someone tried to send an email fraudulently.. and if it is the latter, what should I do about it?
The 2nd IP is making me think I have thinks ill-configured as it comes from sendgrid: https://whatismyipaddress.com/ip/168.245.72.219